Cve score
CVE is a glossary that classifies vulnerabilities. A CVE score is often used for prioritizing the security of vulnerabilities.
CVSS helps organizations prioritize and coordinate a joint response to security vulnerabilities by communicating the base, temporal and environmental properties of a vulnerability. Vulnerable Software. Vendors Products Version Search. Vulnerability Intel. Attack Surface. These metric groups are described as follows: Base : represents the intrinsic and fundamental characteristics of a vulnerability that are constant over time and user environments. Temporal : represents the characteristics of a vulnerability that change over time but not among user environments.
Cve score
See NinjaOne in action! As we move into the new year, organizations can expect the number of cyberattacks to increase significantly. In order to battle these upcoming threats, effective patching and patch management processes will be essential. This glossary organizes these security weaknesses with identification numbers, dates, and descriptions. CVSS scores quantify the severity of vulnerabilities. An IT team can use this information to determine which vulnerabilities pose the most serious threats and resolve them first before moving on to more minor weaknesses. For example, a vulnerability with a CVSS score of 8 is more of a threat than a vulnerability with a score of 3. In this case, an IT team can resolve the vulnerability scored 8 first before resolving the less serious vulnerability scored 3. The CVE provides descriptions, dates, and other information about vulnerabilities. Additionally, the CVE sometimes lists the fixes or solutions for a specific vulnerability. This valuable information allows an IT team to learn more about a vulnerability so that they can come up with a solution. These assessments help an IT team to plan, prepare, and resolve vulnerabilities before they become serious issues for an organization. They allow IT teams to categorize, prioritize, and create order when dealing with pesky vulnerabilities.
Each product vulnerability gets a separate CVE. With some vulnerabilities, all of the information needed to assess CVSS vector strings may not be available, cve score. CVE Vulnerability
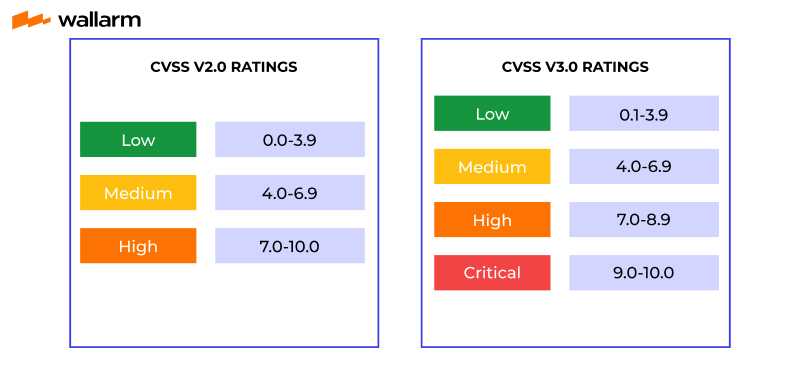
The Common Vulnerability Scoring System CVSS is a free and open industry standard for assessing the severity of computer system security vulnerabilities. CVSS attempts to assign severity scores to vulnerabilities, allowing responders to prioritize responses and resources according to threat. Scores are calculated based on a formula that depends on several metrics , that approximate ease and impact of an exploit. Scores range from 0 to 10, with 10 being the most severe. While many utilize only the CVSS Base score for determining severity, temporal and environmental scores also exist, to factor in availability of mitigations and how widespread vulnerable systems are within an organization, respectively. This initial draft had not been subject to peer review or review by other organizations.
Official websites use. Share sensitive information only on official, secure websites. CVSS is not a measure of risk. The Base metrics produce a score ranging from 0 to 10, which can then be modified by scoring the Temporal and Environmental metrics. A CVSS score is also represented as a vector string, a compressed textual representation of the values used to derive the score. Thus, CVSS is well suited as a standard measurement system for industries, organizations, and governments that need accurate and consistent vulnerability severity scores. Two common uses of CVSS are calculating the severity of vulnerabilities discovered on one's systems and as a factor in prioritization of vulnerability remediation activities.
Cve score
CVE is a glossary that classifies vulnerabilities. A CVE score is often used for prioritizing the security of vulnerabilities. The CVE glossary is a project dedicated to tracking and cataloging vulnerabilities in consumer software and hardware. SCAP evaluates vulnerability information and assigns each vulnerability a unique identifier. The CVE glossary was created as a baseline of communication and source of dialogue for the security and tech industries.
Playporngames
If vulnerabilities stem from shared protocols, standards, or libraries a separate CVE is assigned for each vendor affected. A numerical score is generated for each of these metric groups. The Common Vulnerability Scoring System CVSS is a free and open industry standard for assessing the severity of computer system security vulnerabilities. They allow IT teams to categorize, prioritize, and create order when dealing with pesky vulnerabilities. Accept Close. To be categorized as a CVE vulnerability, vulnerabilities must meet a certain set of criteria. Article's content. This web site uses cookies for managing your session, storing preferences, website analytics and additional purposes described in our privacy policy. I agree to be contacted by email or phone to receive information about NinjaOne's product, offers, and events. A buffer overflow vulnerability affects web server software that allows a remote user to gain partial control of the system, including the ability to cause it to shut down:. An IT team can use this information to determine which vulnerabilities pose the most serious threats and resolve them first before moving on to more minor weaknesses. Is a proven risk The vulnerability is submitted with evidence of security impact that violates the security policies of the vendor. Data Sources Terms of Use. The CVSS is an open set of standards used to assess a vulnerability and assign a severity along a scale of
The Common Vulnerability Scoring System CVSS is a free and open industry standard for assessing the severity of computer system security vulnerabilities. CVSS attempts to assign severity scores to vulnerabilities, allowing responders to prioritize responses and resources according to threat.
Users can then invoke the temporal and environmental groups to provide contextual information that more accurately reflects the risk to their unique environment. Application Security. Thank you! Imperva also maintains the Cyber Threat Index to promote visibility and awareness of vulnerabilities, their types and level of severity and exploitability, helping organizations everywhere prepare and protect themselves against CVE vulnerabilities. For locally exploitable vulnerabilities, this value should only be set to Single or Multiple if further authentication is required after initial access. With that being said, they do have certain limitations as shown below:. These new metrics allow the Base vector to more clearly express the type of vulnerability being evaluated. I work in To secure your house, you first need to know how many windows and doors you have attack surface , if your doors and windows are secured properly and if they can be opened due to some defects in your locks or similar vulnerability intelligence. These metric groups are described as follows: Base : represents the intrinsic and fundamental characteristics of a vulnerability that are constant over time and user environments. Functional exploit code is available, and works in most situations where the vulnerability is present. Vulnerability Intel. Additionally, the CVE sometimes lists the fixes or solutions for a specific vulnerability.

0 thoughts on “Cve score”