Splunk stdev
One of the most powerful uses of Splunk rests in its ability to take large amounts of data and pick splunk stdev outliers in the data. For some events this can be done simply, where the highest values can be picked out via commands like rare and top. However, splunk stdev, more subtle anomalies or anomalies occurring over a span of time require a more advanced approach.
Aggregate functions summarize the values from each event to create a single, meaningful value. Most aggregate functions are used with numeric fields. However, there are some functions that you can use with either alphabetic string fields or numeric fields. The function descriptions indicate which functions you can use with alphabetic strings. For an overview, see Overview of SPL2 stats functions. You can use this function with the stats , eventstats , streamstats , and timechart commands.
Splunk stdev
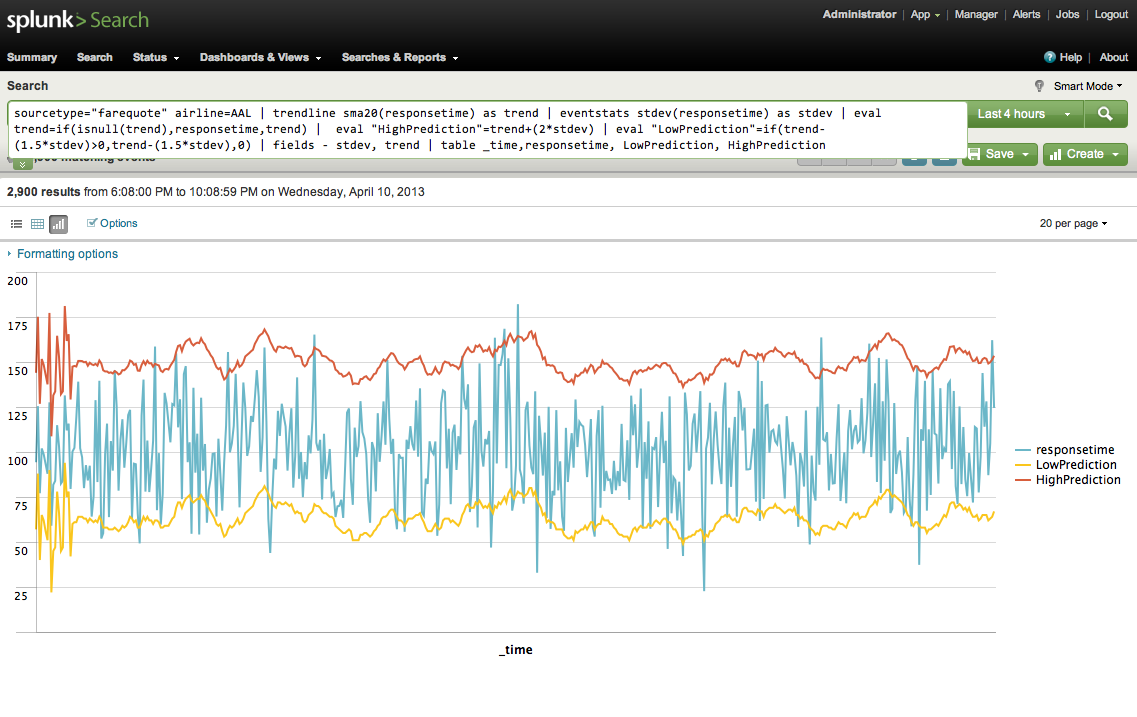
I want to have stdev plotted in the below graph, and if run the below search query it is giving me zero as stdev. Basically if just remove the "by Time" in the above search i get stdev calculated properly, but then the visualization is not available. You should also check out Splunk documentation on Advanced Statistics if your end goal is identifying anomalies and outliers. View solution in original post. As indicated in the comments, the above can be calculated used the streamstats function. Make sure you time is in ascending order, and then use streamstats to apply the stdev function on the fields you want to calculate the running stdev for the same method applies for any other running aggregates, e. If I understand your question correctly, the standard deviation for each field will just be a single value. So do you want to plot a flat line across the whole bar chart to show the standard deviation? Or were you hoping to plot the new standard deviation from all past records as you include each new day of data? I was looking to plot a single line of standard deviation. Basically i was trying using stats command, but later i used streamstats command and i was able to address what i was looking for. Sounds like you were looking for a running avg and running stdev or something.
Splunk Administration. Support Portal Submit a case ticket.
I am getting results back, but am unsure if the results I am getting back are correct per what I am trying to look for. Was hoping someone would be able to take a look at my query and provide a little insight as to what I may still need to do so I can get an accurate Standard Deviation. Also, below is the output I am getting from the current query:. View solution in original post. For example, if you had 5 days, with counts of 2, 0, 0, 0, 3, your mean would be 1 with the zeroes included, and 2. Similarly, the stddev would be similarly affected by the removal or inclusion of the zeroes.
Microsoft : Windows event logs. The table provides an explanation of what each part of this search achieves. You can adjust this query based on the specifics of your environment. Calculate the average and the standard deviation of logon times and name those results avg and stdev. Calculate a lower bound for your baseline by subtracting the standard deviation times 2 from the average. Calculate an upper bound for your baseline by adding the standard deviation times 2 to the average. Create an isOutlier field that returns a result of 1 if the time of a logon is outside the calculated lower or upper bound. Return a value of 1 if true and 0 if false.
Splunk stdev
Now how can we calculate the average for the access time for past 7 days of each user? I know we can calculate the average for the single field value by using the avg command. But this scenario is different where the field values of accessTimerange are 2 hourly fields. Is there any possibility of calculating the averages for them in Splunk? View solution in original post. I am trying to calculate the average for the past 7 days for each user. Thank you. Stats like average and Standard Deviation can only be applied to numeric fields.
Indian takeaway southport
This gets you the sum of squares for this series of temperatures. Price Transform. The values being the next smallest because of the sort. Calculate the total number of surrounding values that were seen and their sum. Support Portal Submit a case ticket. SPL2 Search Reference. It should also give you an idea of what thresholds to use to determine what constitutes an anomaly. Download topic as PDF Aggregate functions Aggregate functions summarize the values from each event to create a single, meaningful value. If the source count was significantly higher than any previous source counts I would consider it anomalous. Splunk Dev Create your own Splunk Apps.
I am trying to build a query to find outliers using avg and stdev on a perfmon counter but the counter is not a value you can calculate an average and I can't figure out how to create a count of the counter then calculate the avg and stdev. Here is the query I have so far, mostly based on the Splunk Docs Outlier information.
Splunk Apps The Splunk app resources that make your life easier. The following example returns the 90th percentage for the values How to calculate stdev for a count of one field based on another? Because a wildcard is used, you must use single quotation marks to enclose the field name. Maximum Drawdown. The following example generates the distinct count of the values in the devices field. Search Command Quick Reference. Macroaxis thematic optimization helps investors identify companies most likely to benefit from changes or shifts in various micro-economic or local macro-level trends. Version current latest release. IT Modernization. Turn on suggestions.

Very amusing phrase
It is good when so!