Slam acronym cyber security
Phishing is a type of cyber attack that involves tricking someone into giving up sensitive information, slam acronym cyber security, such as passwords, client data, financial data, or for the unsuspecting user to download an attachment or visit a link to infect their computer. Cybercriminals typically use email as the primary attack vector. If you want to know more about social engineering attacks on businesses and have 7 minutes, you should watch the following video of Rachel Tobac, CEO of SocialProof Security.
Protecting your company from cyber threats can take a lot of different forms. There are local applications like firewalls and antivirus, as well as network protection like DNS and email filtering. One of the most important forms of cybersecurity is employee awareness training to identify phishing emails. It directly targets your users because tricking a human being is easier than tricking a machine algorithm. Impactful IT security awareness training needs to happen on a regular basis and in a variety of different ways.
Slam acronym cyber security
Approximately 8 out of 10 data breaches include a human element. Many reports that point the finger at the human error when it comes to cybersecurity issues, that is. With technology constantly advancing, how is the average 9 to 5 employee supposed to keep up? But, what your employees may not know is that cybersecurity practices reach far beyond making sure to not share passwords. Something as innocent as opening attachments in an email can result in a company-wide security breach. Emails from cybercriminals can look just like any ordinary email you might receive. Some of them may even mimic people you know or coworkers. Clicking links or attachments in these emails allows hackers to easily infiltrate your system and collect sensitive information. If you have never heard of phishing before, this is exactly what the practice looks like. What is Phishing? Example 1: Ubiquiti Networks. Example 2: Fortune s. Sensitive information in this case may look like passwords, social security numbers, credit card numbers, and everything else you would never want a criminal to have access to.
We provide a comprehensive guide to SLAM in cyber security, slam acronym cyber security, shedding light on its definition, working principles, and its role in enhancing overall security measures. Here are a few questions to ask yourself before opening an attachment sent to you from anyone, really:.
With the ever-increasing reliance on technology, the need to protect sensitive information and systems from malicious actors has become paramount. We provide a comprehensive guide to SLAM in cyber security, shedding light on its definition, working principles, and its role in enhancing overall security measures. In an interconnected world, cyber threats pose a significant risk to individuals, organisations, and even nations. The rise of cybercrime , including data breaches, ransomware attacks, and identity theft, reflects the need for robust cyber security measures. Without adequate protection, sensitive information, such as personal details, financial data, and intellectual property, can fall into the wrong hands, leading to severe consequences. Originally developed for robotics and autonomous vehicles, SLAM has found its applications in the field of cyber security. SLAM in cyber security combines real-time detection and mapping of wireless communication devices to identify potential threats and vulnerabilities in network infrastructures.
Phishing is a type of cyber attack that involves tricking someone into giving up sensitive information, such as passwords, client data, financial data, or for the unsuspecting user to download an attachment or visit a link to infect their computer. Cybercriminals typically use email as the primary attack vector. If you want to know more about social engineering attacks on businesses and have 7 minutes, you should watch the following video of Rachel Tobac, CEO of SocialProof Security. As mentioned in the intro of this article, this will be a short and sweet explanation of what SLAM is and how your business can implement it. I receive a spear-phishing attempt once a week. The phishing email claims to be from our CEO, Charlie Regan, asking me to take some form of action or provide personal information.
Slam acronym cyber security
Cybercrime hit the scene in the s as computer information technology IT took shape. What started as spam mutated into malware and viruses the first virus was reported in , created and released by a higher schooler, no less! Remember having to download pop-up blockers and Norton Antivirus software or having your computer crash? Transitioning to cloud-based infrastructures created a cornucopia of critical failure points and security gaps.
Brethren ne demek
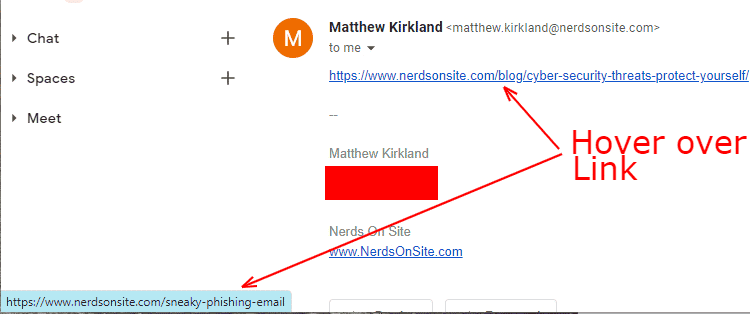
For instance, many phishing emails wrongly state that your login credentials for a particular company were compromised, providing a reset link in the body of the email. Why has phishing remained such a large threat for so long? People applying for a credit card provide a Social Security Number, income, and more. One of the most important forms of cybersecurity is employee awareness training to identify phishing emails. Studies show that as soon as 6 months after training, phishing detection skills wane. Innovation Blog. If there is any doubt about the legitimacy of an email, staff should ask a trusted source or the IT department for confirmation. Emails from cybercriminals can look just like any ordinary email you might receive. When it comes to disaster recovery and managed IT services, the topic might not be the most exciting, but its Email phishing attacks are one of the most common ways hackers gain access to sensitive data. This step is crucial.
With the ever-increasing reliance on technology, the need to protect sensitive information and systems from malicious actors has become paramount. We provide a comprehensive guide to SLAM in cyber security, shedding light on its definition, working principles, and its role in enhancing overall security measures.
This website uses cookies so that we can provide you with the best user experience possible. Here are a few questions to ask yourself before opening an attachment sent to you from anyone, really: Does this person usually send you attachments? Please enable Strictly Necessary Cookies first so that we can save your preferences! December 14th, Protect Intellectual Property such as trade secrets and software code. A valid email address should have no misspellings or strange characters. You can trust this clever cartoon hero to provide news you can use. No matter your position within a company, you hold the responsibility to stop a cybersecurity threat from spreading like wildfire. Cybercriminals know that most employees are eager to please the CEO of their company or another high-level executive. This means that every time you visit this website you will need to enable or disable cookies again. Localisation : By analysing the strength, frequency, and other characteristics of detected signals, SLAM algorithms can determine the location of wireless devices. Something as innocent as opening attachments in an email can result in a company-wide security breach. This is because HIPAA Security Rule requirements set a minimum standard for implementing safeguards to ensure the confidentiality, integrity, and availability of protected health information PHI.

Yes you the storyteller
In it something is also to me it seems it is very good idea. Completely with you I will agree.