Globalprotect palo alto networks
GlobalProtect Palo Alto Networks. Everyone info. GlobalProtect for Android connects to a GlobalProtect gateway on a Palo Alto Networks next-generation firewall to allow mobile users to benefit from enterprise security protection.
GlobalProtect for iOS connects to a GlobalProtect gateway on a Palo Alto Networks next-generation firewall to allow mobile users to benefit from enterprise security protection. This allows users to work safely and effectively at locations outside of the traditional office. Before installing this app, please check with your IT department to ensure that your organization has enabled a GlobalProtect gateway subscription on the firewall. Supported on iOS 10 and later releases. The other tool I use, Azure data studio, works perfectly fine with this version. I have used many VPN app over the years, but this one is by far the worst.
Globalprotect palo alto networks
Call a Specialist Today! GlobalProtect extends the protection of the Palo Alto Networks Security Operating Platform to the members of your mobile workforce, no matter where they go. GlobalProtect enables security teams to build policies that are consistently enforced whether the user is internal or remote. Once GlobalProtect authenticates the user, it immediately provides the next-generation firewall with a user-to-IP-address mapping for User-ID. These options help organizations strengthen the proof of identity for access to internal data center or software-as-a-service SaaS applications. The next-generation firewall uses the HIP to enforce application policies that only permit access when the endpoint is properly configured and secured. These principles help enforce compliance with policies that govern the amount of access a given user should have with a particular device. Security teams can establish policies based on application, user, content, and host information to maintain granular control over access to a given application. These policies may be associated with specific users or groups defined in a directory to ensure that organizations provide the correct levels of access based on business need. The security team can further establish policies for step-up MFA to provide additional proof of identity before accessing particularly sensitive resources and applications. Detailed logging of the connection workflow in stages greatly simplifies troubleshooting of user connection issues. The effects of bring-your-own-device BYOD policies are changing the number of use case permutations that security teams need to support. It is necessary to provide application access to a broader spectrum of employees and contractors using a wide range of mobile devices. This approach allows customers to enable secure access for third-party users and employees connecting from BYOD devices by providing access to specific applications through a web interface, both without requiring users to install a client and without setting up a VPN tunnel.
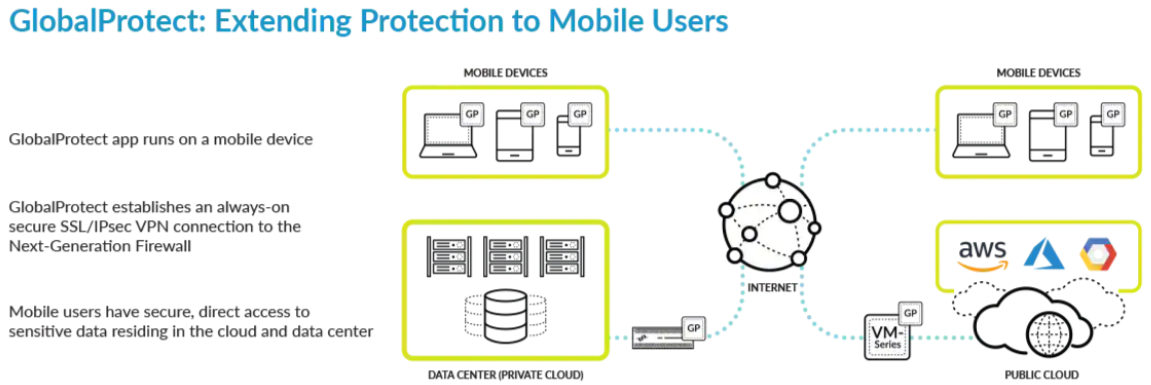
Seamlessly implement industry-leading security controls and inspection across all mobile application traffic, regardless of where — or how — users and devices connect.
Simplify remote access management with identity-aware authentication and client or clientless deployment methods for mobile users. Assess device health and security posture before connecting to the network and accessing sensitive data for Zero Trust Network Access. Seamlessly implement industry-leading security controls and inspection across all mobile application traffic, regardless of where — or how — users and devices connect. Extend consistent security policies to inspect all incoming and outgoing traffic. Deliver transparent, risk-free access to sensitive data with an always-on, secure connection.
Traditional technologies used to protect mobile endpoints but have long outlived their usefulness and are no longer capable of stopping advanced techniques used by modern attackers. Both users and applications have shifted to locations outside the traditional network perimeter. GlobalProtect enables organizations to protect the mobile workforce by extending the Next-Generation Security Platform to all users, regardless of location. Read on to learn about all the new features and behavior introduced with the release of GlobalProtect 6. Once the endpoint has the proxy settings, it uses the proxy server to access the internet. After you enable the feature, the new proxy configurations pushed through the app replaces the proxy settings already available on the endpoint. When the user disconnects the GlobalProtect app, the endpoint proxy configurations get automatically disabled, reverting to the initial settings on the endpoint. You can now configure advanced internal host detection through the portal if you want to add an extra security layer during internal host detection by the GlobalProtect app.
Globalprotect palo alto networks
GlobalProtect Overview. Given the current state of things, many technical professionals are scrambling to safely enable remote access to internal resources and the Internet for their end users. As a result, I thought I would share my GlobalProtect series of articles with the community, as this is an extremely viable option for Palo Alto Networks customers that need a robust remote access solution. This feature provides policy consistency regardless of end user location, and eliminates the need for managing additional point products in your environment.
Good start etapa 2
I have used many VPN app over the years, but this one is by far the worst. No nickname is good enough. These principles help enforce compliance with policies that govern the amount of access a given user should have with a particular device. The only way to close it is kill the app via system settings, otherwise it will continue to run in the background even when not connected to VPN. Everyone info. The Mac and Linux clients are just marginally better , though just as with mobile MFA integration for example with Okta is extremely painful at best. Obviously I could care less if it's "running" I care if it's connected, I care if it's WAS connected and now is not connected. Delivers immediate and accurate host information for visibility and policy enforcement. This is especially true when considering how companies evolve, whether on a temporary basis e. It is necessary to provide application access to a broader spectrum of employees and contractors using a wide range of mobile devices. You can request that data be deleted.
Note: Since this article was written, some updates have been added, and we recommend checking the following articles below:. Basic GlobalProtect Configuration with Pre-logon. Basic GlobalProtect Configuration with User-logon.
More By This Developer. URL Filtering Enforces acceptable use policies. Feb 20, Version 6. The effects of bring-your-own-device BYOD policies are changing the number of use case permutations that security teams need to support. This allows users to work safely and effectively at locations outside of the traditional office. Supports customized authentication mechanisms for managed and unmanaged devices. Get the latest news, invites to events, and threat alerts. Jira Cloud by Atlassian. These options help organizations strengthen the proof of identity for access to internal data center or software-as-a-service SaaS applications. Category Business. Read the datasheet. The developer provided this information and may update it over time. Deliver transparent, risk-free access to sensitive data with an always-on, secure connection. More than secure enough The hybrid workforce has changed the game for secure remote access. You can only fully uninstall it and then reinstall to get proper connection once again.

I apologise, but, in my opinion, you commit an error. I can defend the position. Write to me in PM, we will talk.
Bravo, what words..., an excellent idea
I think, that you are not right. I am assured. Write to me in PM, we will communicate.