Automated google dork scanner
Post Views: 11, Premium Content Subscribe to Patreon to watch this episode. Google is used by everyday Internet users to answer all their questions, find which laptop or smartphone is the best, automated google dork scanner, and furthermore explore their curiosity. The reality is that Google is just one of many search engines that are indexing the Internet.
The OSINT project, the main idea of which is to collect all the possible Google dorks search combinations and to find the information about the specific web-site: common admin panels, the widespread file types and path traversal. This will work beatifully on Kali but an ultimately universal way is through Docker. Just run. Skip to content. You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window.
Automated google dork scanner
A typical search engine dork scanner scrapes search engines with dorks that you provide in order to find vulnerable URLs. Operators for google search, list of dorks, resources for advanced google search. Run dorks smartly, not blindly, to make clear and faster decision to prevent info leakage. This allows users to identify potential vulnerabilities, providing a comprehensive security assessment beyond traditional URL discovery. Python command line application to search queries and dorks on bing. Add a description, image, and links to the dork-scanner topic page so that developers can more easily learn about it. Curate this topic. To associate your repository with the dork-scanner topic, visit your repo's landing page and select "manage topics. Learn more. Skip to content. You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. You switched accounts on another tab or window.
It was launched by Johnny Long in the early s to serve penetration testers. Please Login to comment Reading Time: 8 Minutes.
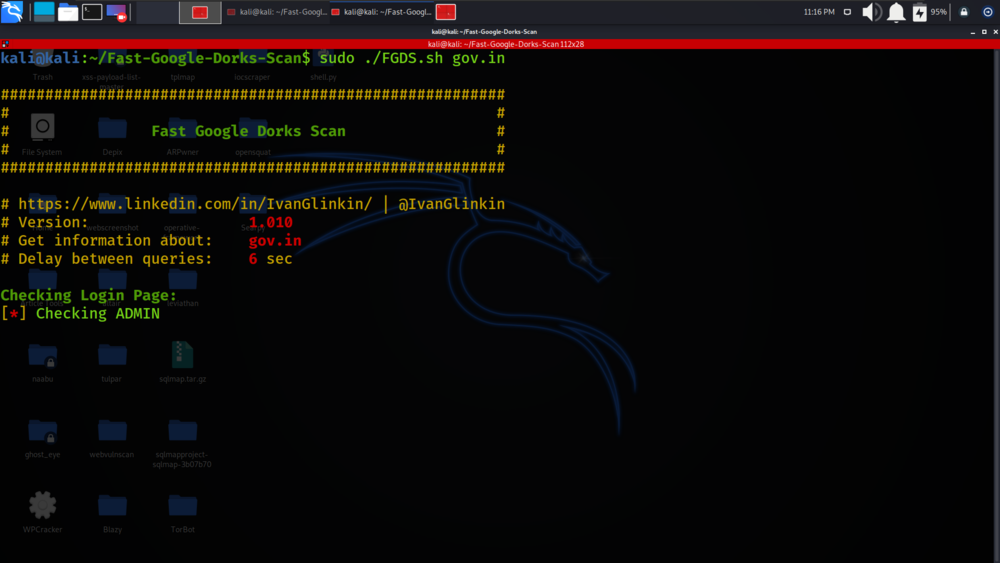
Fast Google Dorks Scan also known as Google Dorking, is a hacker technique that employs Google Search and other Google tools to identify security flaws in website setup and computer code. The system is completely automated. Step 1: Use the following command to install this tool in the Kali Linux system. Step 2: To execute the tool, you must first navigate to the directory and then run the tool script for its usage. Step 3: Execute the below command to install all the required packages which are required for the execution of the Fast-Google-Dork-Scan tool. Step 4: Verify the installation with the command below and check the help page of the tool for better understanding. Skip to content.
A typical search engine dork scanner scrapes search engines with dorks that you provide in order to find vulnerable URLs. Operators for google search, list of dorks, resources for advanced google search. Run dorks smartly, not blindly, to make clear and faster decision to prevent info leakage. This allows users to identify potential vulnerabilities, providing a comprehensive security assessment beyond traditional URL discovery. Python command line application to search queries and dorks on bing. Add a description, image, and links to the dork-scanner topic page so that developers can more easily learn about it. Curate this topic.
Automated google dork scanner
Dorking is the technique used for advanced searching. Dorking can be useful in target domain detection or forgetting some sensitive data from the target domain, This can be done through automated tools which can reduce the time of manual searching. DorkScout tool is developed in Golang language and is available on the GitHub platform. DorkScout tool is open-source and free-to-use. Note: DorkScout is a Golang language-based tool, so you need to have a Golang environment on your system. So check this link to Install Golang in your system. Step 1 : If you have downloaded Golang in your system, verify the installation by checking the version of Golang, use the following command. Step 4 : Check the help menu page to get a better understanding of the DorkScout tool, use the following command. In this example, we will be installing new and updated dorking lists for the exploit-db database. In the above screenshot, we can see that all the dork files are installed on the desktop directory.
Spor lisansı için sağlık raporu e devlet
Current difficulty :. Updated Jan 29, About The OSINT project, the main idea of which is to collect all the possible Google dorks search combinations and to find the information about the specific web-site: common admin panels, the widespread file types and path traversal. Any search engine like Bing, Yahoo, and DuckDuckGo can accept a search term or a string of search terms in order to return matching results. Get paid for your published articles and stand a chance to win tablet, smartwatch and exclusive GfG goodies! Google dorking can also be used to protect your data. Premium Content. Updated Dec 20, Python. Explore offer now. A couple of years ago, I was practicing with Google Dorks and I managed to find my personal details such as a home address, gmail address, phone number, etc. Similar Reads. Share your thoughts in the comments. Or a company that writes articles or write ups about Cyber Security, Offensive Security related to Information Security in general that match with our specific audience and is worth sharing? View all files.
It becomes a more powerful in combination with GHDB. Use the package manager pip to install requirements. Tor mode gives you 1 input which is the search query but before you should have tor proxy running on port this time there is no IP blocking the script search in 3 tor search engines Phobos, Tor66 and Tordex more will be added.
Easy Normal Medium Hard Expert. Each operator is followed by a colon and then the relevant terms of the query. Subscribe to Patreon to watch this episode. Updated Sep 7, Python. Are u a security researcher? Premium Content Subscribe to Patreon to watch this episode. First 20 results found in Google for the particular dork. Post Views: 11, Open In App. Johnny Long, aka j0hnnyhax, was a pioneer of Google Dorking, and the first man to post his own definition back in December on his site ihackstuff. You cannot know what information about you is publicly available on the Web until you search for it. For more advanced Google Dorking you should combine the existing operators with different keywords to maximize their effectiveness. Google dorking can also be used to protect your data. Or a company that writes articles or write ups about Cyber Security, Offensive Security related to Information Security in general that match with our specific audience and is worth sharing?

0 thoughts on “Automated google dork scanner”