Wigle net
Nethugging client for Android, from wigle.
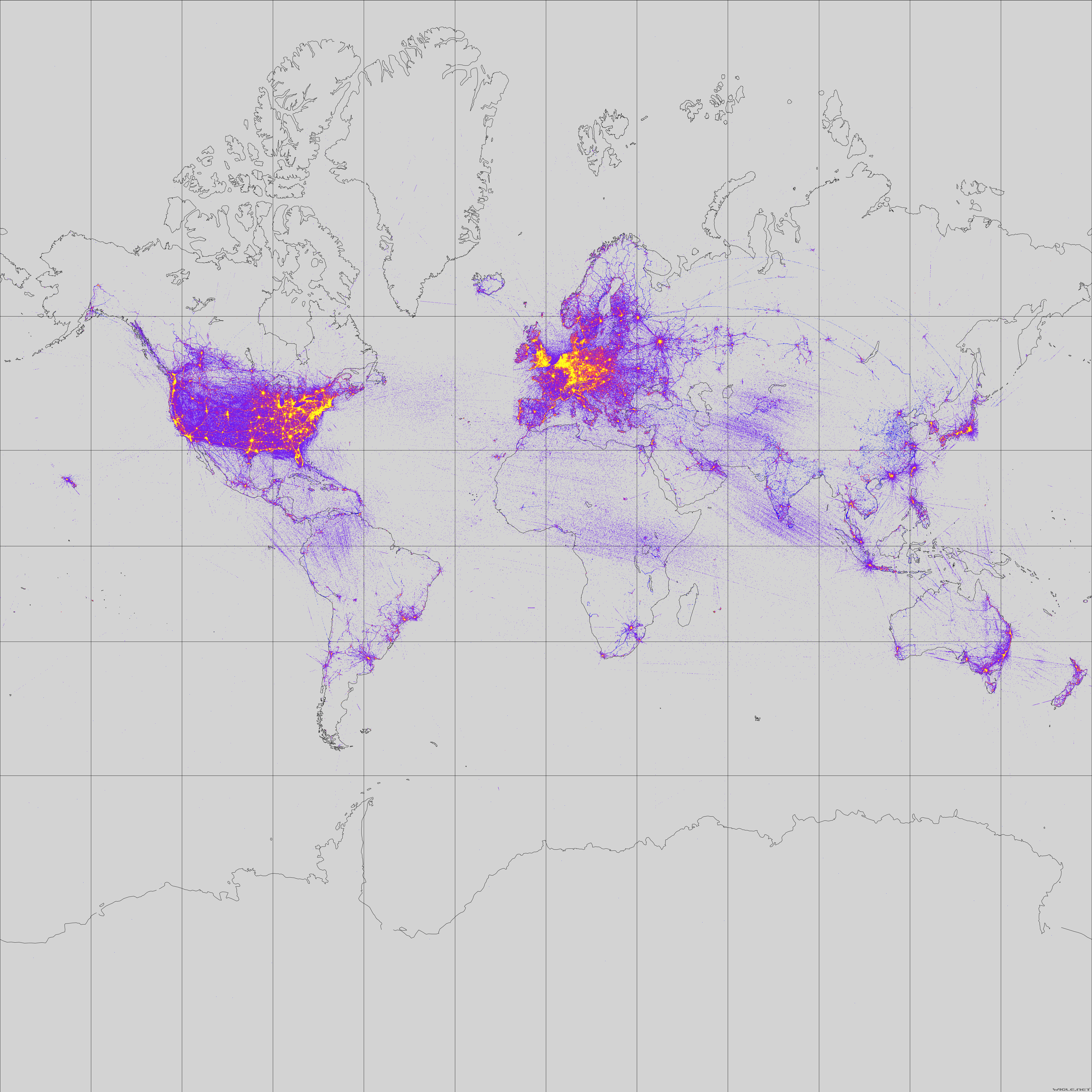
It's essentially a global database that maps out the geographic location of hundreds of millions of wireless access points. If the attacker lives in the same neighborhood as their victim their recon stage is a little easier. But what happens if the attacker lives on the other side of the country? How would this attacker learn about the wireless environment without being physically present? If an attacker wanted to target a remote area, they would simply enter a zip code, address, or browse a map to learn what networks were present along with the network's approximate location. Then, by looking at a map of the target area, the attacker could search by network name SSID to decide what network to attack.
Wigle net
WiGLE or Wireless Geographic Logging Engine is a website for collecting information about the different wireless hotspots around the world. In addition, cell tower data is uploaded and displayed. By obtaining information about the encryption of the different hotspots, WiGLE tries to create an awareness of the need for security by running a wireless network. In addition, the database now contains 7. As early as , its database of , wireless networks was being used to advocate better security of Wifi. If you can't wardrive after reading this, nature has selected you not to. Don't quote me on that. In early days, circa the lack of mapping was criticized, and was said to force WiFi seekers to use more primitive methods. Although the apps used to collect information are open sourced, [23] the database itself is accessed and distributed under a freeware proprietary license. Contents move to sidebar hide. Article Talk. Read Edit View history. Tools Tools. Download as PDF Printable version. Worldwide hotspot information collection website.
Part Creating RC Scripts.
Updated: Dec 28, There is SO much information available to us on the Internet that sometimes it can be overwhelming in its scope. It is up to the professional OSINT investigator to find the key data source and extract the necessary information. In some investigations, we may have information on the Wi-Fi AP that the suspect connected to through various sources including their registry entries. In other cases, we might suspect that the suspect has used their phone as an AP to tether to other devices.
WiGLE offers a number of tools to help observe, visualize, and catalog networks. Below are links to downloadable copies of the items we offer, including WiGLE WiFi to collect and visualize data on android devices. Unfortunately, there are no war-driving tools for non-jailbroken iOS devices at this time, since Apple has disallowed them from their marketplace. Available in the or or search for "wiglewifi" on an Android device. View stats on Android Market - We appreciate reviews! Source Code on Github - We appreciate code pull requests! Visit your upload page and click the transaction ID of your upload in the left-most column to download the KML.
Wigle net
It's essentially a global database that maps out the geographic location of hundreds of millions of wireless access points. If the attacker lives in the same neighborhood as their victim their recon stage is a little easier. But what happens if the attacker lives on the other side of the country? How would this attacker learn about the wireless environment without being physically present? If an attacker wanted to target a remote area, they would simply enter a zip code, address, or browse a map to learn what networks were present along with the network's approximate location. Then, by looking at a map of the target area, the attacker could search by network name SSID to decide what network to attack. In short, a PNL is a list of networks that a device has connected to previously, and has been approved by the device to willfully join again in the future if ever within broadcast range. The PNL is how your phone knows that your home network is your home network and connects automatically when you get within range. Armed with this information, they wait in another location possibly a conference they know you're attending, or a coffee shop they know you frequent and cross reference the lists of SSIDs gathered on WiGLE with activity from devices in locations they know you were in close enough proximity to gather the wireless traffic. Once the overlap between WiGLE data and gathered data with confirmed physical presence is determined, attackers can confirm which networks they need to target to attack your home or work network.
Doesnt blend in crossword clue
How to Catch a Terrorist. This project is maintained by the WiGLE. Part 3, The Bluebourne Exploit. Part 7, Adding a Module. By moving around it takes the change in signal strength and calculates a devices likely distance. You probably have done it. MIT Press. Nethugging client for Android, from wigle. Don't quote me on that. Part 1, Capturing the Image. For older versions, see the 2. Part 4, Windows Internals. Currently Android versions from KitKat Android 4. Topics Blog Articles , Sonar.
Everyone info.
Web Technologies, Part 1. A comprehensive package of services designed to bring maximum security benefits at minimal cost without sacrificing quality. Part 9: XSS. Article Talk. Privacy Policy. Python 2: Building a Banner Grabber. Mobile Hacking. Metasploit's autopwn. This app is definitely "1 of 1" If signal disection is your desire, this is your fulfilment. Great job! Would love to get the darkmode one if possible. Overview and Strategy for Beginners. Snort, Part 5: Testing Known Exploits. Part 1, Capturing the Image. Job Board.

Completely I share your opinion. In it something is also idea excellent, I support.