Which security related phrase relates to the integrity of data
This specification describes mechanisms for ensuring the authenticity and integrity of Verifiable Credentials and similar types of constrained digital documents using cryptography, especially through the use of digital signatures and related mathematical proofs.
How might the goals of a basic network management not be well-aligned with the goals of security? A company has an annual contract with an outside firm to perform a security audit on their network. The purpose of the annual audit is to determine if the company is in compliance with their internal directives and policies for security control. Select the broad class of security control that accurately demonstrates the purpose of the audit. A Managerial is the control that gives oversight of the information system including selection of other security controls. An example of this type of control is regular scans and audits. C Detect refers to performing ongoing proactive monitoring to ensure that controls are effective and capable of protecting against new types of threats.
Which security related phrase relates to the integrity of data
Biba in , [1] is a formal state transition system of computer security policy describing a set of access control rules designed to ensure data integrity. Data and subjects are grouped into ordered levels of integrity. The model is designed so that subjects may not corrupt data in a level ranked higher than the subject, or be corrupted by data from a lower level than the subject. In general the model was developed to address integrity as the core principle, which is the direct inverse of the Bell—LaPadula model which focuses on confidentiality. This security model is directed toward data integrity rather than confidentiality and is characterized by the phrase: "read up, write down". This is in contrast to the Bell-LaPadula model which is characterized by the phrase "read down, write up". In the Biba model, users can only create content at or below their own integrity level a monk may write a prayer book that can be read by commoners, but not one to be read by a high priest. Conversely, users can only view content at or above their own integrity level a monk may read a book written by the high priest, but may not read a pamphlet written by a lowly commoner. Another analogy to consider is that of the military chain of command. A General may write orders to a Colonel, who can issue these orders to a Major. In this fashion, the General's original orders are kept intact and the mission of the military is protected thus, "read up" integrity. Conversely, a Private can never issue orders to his Sergeant, who may never issue orders to a Lieutenant, also protecting the integrity of the mission "write down". The Biba model defines a set of security rules, the first two of which are similar to the Bell—LaPadula model.
Hashing is a process described by a hashing algorithm that calculates an identifier for the transformed data using a cryptographic hash function. You are consulting on threat intelligence solutions for a supplier of electronic voting machines. A streamlined version of this design pattern emerged insuch that a developer would only need to include a single JSON-LD Context to support all modern cryptographic suites.
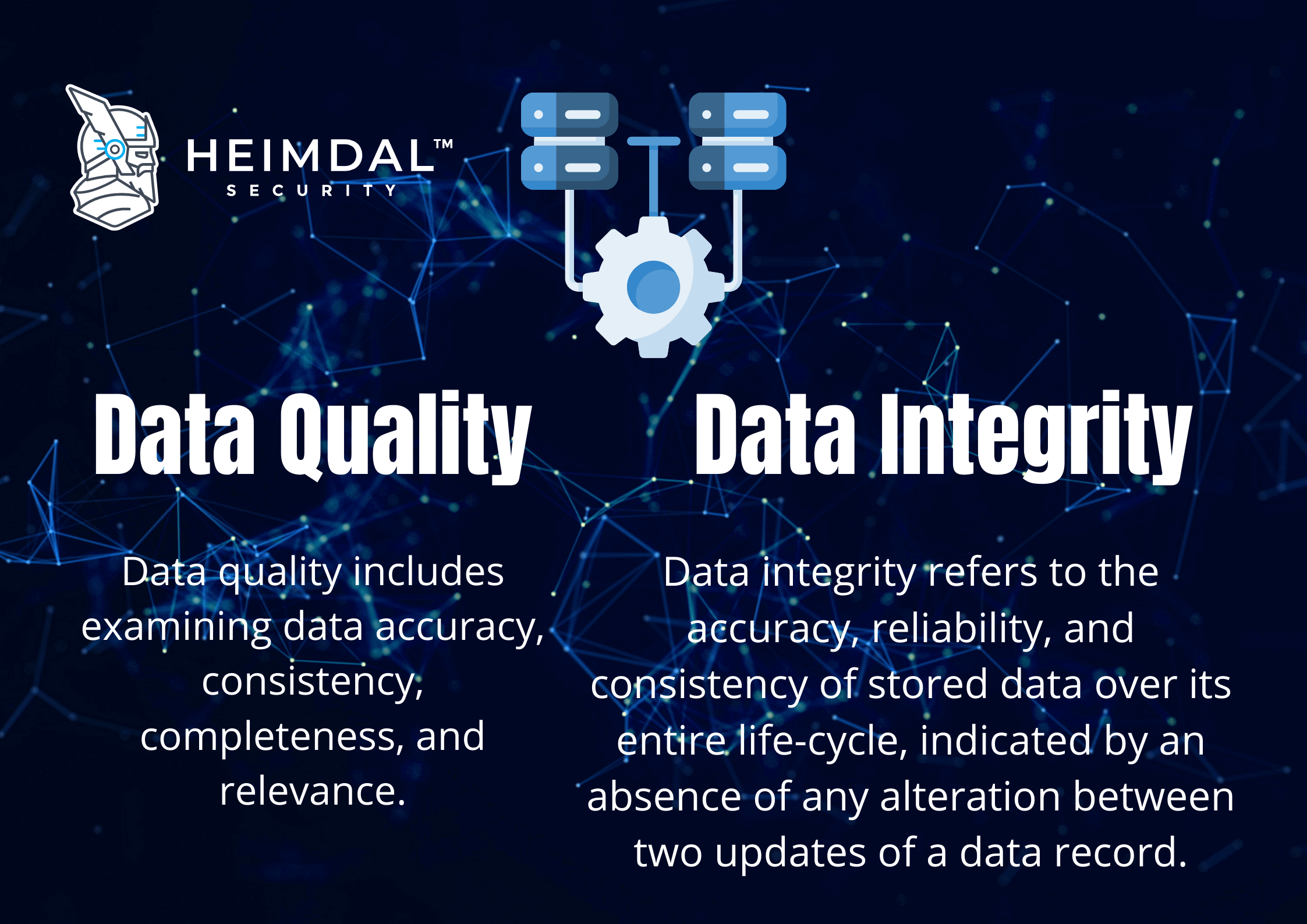
Integrity means that any data is stored and transferred as intended and that any modification is authorized. Integrity is part of the CIA triad. Information is accessible only to those authorized to view or modify it. Detect refers to performing ongoing proactive monitoring to ensure that controls are effective and capable of protecting against new types of threats. Identify covers developing security policies and capabilities, and evaluating risks, threats, and vulnerabilities and recommend security controls to mitigate them. The implementation of cybersecurity resilience to restore systems and data if other controls are unable to prevent attacks. A multinational company manages a large amount of valuable intellectual property IP data, plus personal data for its customers and account holders.
Data integrity refers to the accuracy and consistency of data over its lifecycle. Without accurate information, companies are not able to use it in any way. Data integrity can be compromised and checked for errors. Validation procedures are used to ensure the data is not changed during transfer or replication. Schedule a demo to learn how we can help. Data integrity can mean one of two things: either the state that a data set is in, or it refers to processes used for accuracy. Error checking and validation methods are an example of this. Maintaining data integrity is important because it ensures that the company can recover and search for information, trace to its origin, connect with other databases without errors or mistakes.
Which security related phrase relates to the integrity of data
Information security relies on keeping data secure, integral, and available—but tradeoffs are necessary in real-world scenarios. The model has nothing to do with the U. Central Intelligence Agency; rather, the initials stand for the three principles on which infosec rests:.
Baldurs gate fighter/mage
Cryptographic suite implementers are urged to consider appropriate use of data opacity when designing their suites, and to weigh the design trade-offs when making application data opaque versus providing access to cryptographic data at the application layer. Often, just the cryptographic suite name e. Open permissions refers to misconfigured access rights for data folders, network file shares, and cloud storage. When a link to an external resource is included in a conforming secured document , it is desirable to know whether the resource that is identified has changed since the proof was created. The controller document does not express revoked keys using a verification relationship. The way in which a transformation, namely canonicalization, is performed can affect the privacy characteristics of a system. The IT department head returns from an industry conference feeling inspired by a presentation on the topic of cybersecurity frameworks. Example 19 : An integrity-protected image that is associated with an object. Everything else in this specification is normative. Why use non-credential vulnerability scans?
By following the process, organizations not only ensure the integrity of the data but guarantee they have accurate and correct data in their database.
Parametric versioning specifies the particular cryptographic parameters that are employed in a cryptographic suite. Examine each attack vector. Because two parties can hash the same data and compare checksums to see if they match, hashing can be used for data verification in a variety of situations, including password authentication. A cryptosuite instance is instantiated using a cryptosuite instantiation algorithm and is made available to algorithms in an implementation-specific manner. The ip command is a more powerful command in Linux and gives options for managing routes as well as the local interface configuration. In the example above, the secretKeyMultibase value starts with the letter z , which is the Multibase header that conveys that the binary data is basebtc-encoded using the Bitcoin base-encoding alphabet. To assess likelihood and impact, you must identify both the vulnerability and the threat posed by a potential exploit. If the verification is successful, the server has cryptographically determined that the invoker is authorized to access the protected resource. Issue 38 : Determine how cryptographic suites are named and versioned pr exists before CR. This particular association indicates that the issuer or holder , respectively, is the controller of the verification method used to verify the proof. A controller document can express verification methods , such as cryptographic public keys , which can be used to authenticate or authorize interactions with the controller or associated parties. What type of business unit can be used to manage such important and complex security requirements? Select all that apply. How to fix a software vulnerability?

0 thoughts on “Which security related phrase relates to the integrity of data”