Vpn wikipedia
A virtual private network VPN service provides vpn wikipedia proxy server to help users bypass Internet censorship such as geoblocking and users who want to protect their communications against data profiling or MitM attacks on hostile networks. A wide variety of entities provide "VPNs" for several purposes. But depending on the provider and the application, vpn wikipedia, they do not always create a true private network.
Mobile VPNs are used in environments where workers need to keep application sessions open at all times, throughout the working day, as they connect via various wireless networks, encounter gaps in coverage, or suspend-and-resume their devices to preserve battery life. A conventional VPN cannot survive such events because the network tunnel is disrupted, causing applications to disconnect, time out, [1] fail, or even the computing device itself to crash. A VPN maintains an authenticated, encrypted tunnel for securely passing data traffic over public networks typically, the Internet. Makers of mobile VPNs draw a distinction between remote access and mobile environments. A remote-access user typically establishes a connection from a fixed endpoint, launches applications that connect to corporate resources as needed, and then logs off.
Vpn wikipedia
View more global usage of this file. This file contains additional information, probably added from the digital camera or scanner used to create or digitize it. If the file has been modified from its original state, some details may not fully reflect the modified file. File:Virtual Private Network overview. Render this image in Marathi mr Ukrainian uk default language. This is a file from the Wikimedia Commons. Information from its description page there is shown below. Commons is a freely licensed media file repository. You can help. Summary Description Virtual Private Network overview.
Network-to-network tunnels often use passwords or digital certificates. Tom's Guide. Width
Our secure VPN sends your internet traffic through an encrypted VPN tunnel to keep your browsing data safe, even over public or untrusted internet connections. As a Swiss VPN provider, we do not log user activity or share data with third parties. Our anonymous VPN service keeps your browsing history private and enables an internet without surveillance. Proton VPN breaks down the barriers of internet censorship, allowing you to access restricted online content. Our goal is to make online privacy accessible to all.
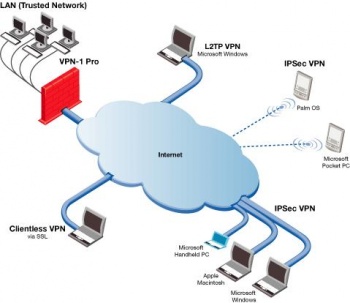
A virtual private network , or VPN is a set of technologies which are used to link computers to create a private network. Another network is used to carry the data, which is encrypted. The carrier network will see the packets of data which it routes. To the users of the VPN, it will look like the computers were directly connected to each other. In a business context, VPNs are often used to connect different office locations or to allow people working from outside the company network to access its resources.
Vpn wikipedia
What does a VPN do? What is VPN encryption? What are VPN protocols? How VPNs unblock streaming sites 5. VPNs in a nutshell 6. Industry rankings 7.
Conor mcgregors last fight
Retrieved January 19, Lifehacker Australia. NetMotion Software. The government of Iran began blocking access to non-government sanctioned VPNs in March , [8] a few months prior to the elections , to "prosecute users who are violating state laws" and "take offenders to national courts under supervision of judiciary service". Tools Tools. Retrieved September 3, Blocking VPN access can be done a few different ways. In a positive review published by Tom's Guide in October , the reviewer concluded that "NordVPN is affordable and offers all the features that even the hardcore VPN elitists will find suitable". A remote-access user typically establishes a connection from a fixed endpoint, launches applications that connect to corporate resources as needed, and then logs off. Some mobile VPNs offer additional "mobile-aware" management and security functions, giving information technology departments visibility and control over devices that may not be on the corporate premises or that connect through networks outside IT's direct control. Retrieved: February 5, Tunnel endpoints must be authenticated before secure VPN tunnels can be established. Yes [c].
NordVPN is developed by Nord Security Nordsec Ltd , a company that creates cybersecurity software and was initially supported by the Lithuanian startup accelerator and business incubator Tesonet.
Unlike other free VPNs, there are no catches. VPNs cannot make online connections completely anonymous, but they can increase privacy and security by encrypting all communication between remote locations over the open Internet. We believe privacy and security are fundamental human rights, so we also provide a free version of Proton VPN to the public. No [24] [25] [26]. Description [ edit ] Blocking VPN access can be done a few different ways. Supports Obfsproxy Whether the service has an implementation of the Tor subproject Obfsproxy. Additionally, VPNs provide a safe and encrypted connection for employees to access company resources, protecting sensitive data from cyber threats. Proceedings on Privacy Enhancing Technologies. Hidden categories: CS1 Simplified Chinese-language sources zh-hans Articles with short description Short description is different from Wikidata Commons category link from Wikidata. IPv6 Leak Protection. In addition we do not log bandwidth usage, session data or requests to our DNS servers. Dedicated [75]. Retrieved March 14, A limitation of traditional VPNs is that they are point-to-point connections and do not tend to support broadcast domains ; therefore, communication, software, and networking, which are based on layer 2 and broadcast packets , such as NetBIOS used in Windows networking , may not be fully supported as on a local area network.

You commit an error. I suggest it to discuss. Write to me in PM.
At me a similar situation. Is ready to help.