Trellix endpoint security
This extension is intended for use with Trellix Endpoint Security Web Control software to provide color-coded URL safety ratings and blocking trellix endpoint security malicious web-page navigation and suspicious file downloads.
Trellix Endpoint Security provides aggressive robust protection for every endpoint in an enterprise organization. Trellix uses dynamic threat intelligence and mounts a superb defense across the complete threat lifecycle. This solution will keep your organization more secure and resistant to any possible threat of risks. Trellix offers an amalgamated suite of next-generation endpoint security tools. These tools give users the benefit of machine learning, intuitive intelligence, and greater assistance to ensure their networks are being protected non-stop against threats - potential or realized - and can stop attacks before they happen.
Trellix endpoint security
Support and onboarding included. Try it now. This powerful combination delivers actionable intelligence, leverages machine learning, and other advanced techniques to enable continuous monitoring and prevention of cyber attacks. MyDigitals Trellix Enhanced Support stands out by providing a comprehensive EDR-solution specifically designed to meet the unique needs of your organization. It goes beyond mere detection, offering a robust platform that helps prevent threats before they can impact your business operations. With Trellix EDR, you benefit from:. Direct support through phone, email, chat, and remote assistance, including screen sharing, is readily available, ensuring you have the help you need, when you need it. Our optional services, such as Trellix Technical Training Basic and Expert levels , Managed Services, and consultancy for integrating new technologies, adding locations, or conducting a comprehensive Trellix health check with a personalized overview, are designed to enhance your security measures effectively. We offer a pre-configured agent for a live demo. Book a free technical consultation with one of our Trellix engineers to discover how our solutions can strengthen your cybersecurity infrastructure. This service is priced based on the scope of your request. Please contact seller for pricing details.
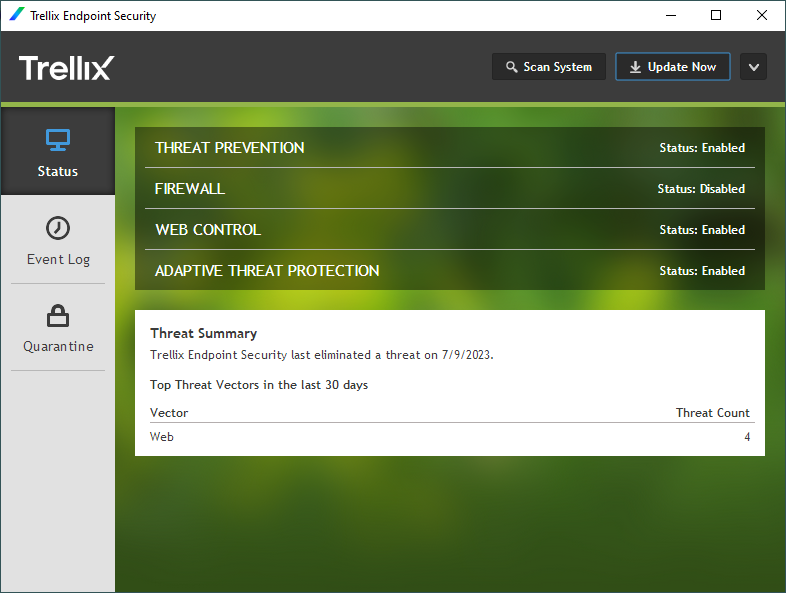
You can also right-click the Trellix icon in the system tray to access various features - such as checking the security status or opening the client. Tweaks Web Protection.
Trellix Endpoint Security HX provides comprehensive defense using multiple engines and customer deployable protection modules to block malware and exploits, detect advanced attacks and provide response tools and techniques developed by the frontline responders. To find unknown and advanced threats, Trellix created machine learning seeded with knowledge from the frontlines of cyber attacks, called MalwareGuard. To stop application and web based exploits, Trellix created a behavior-based analytics engine, called ExploitGuard. Finally, endpoint detection and response EDR capabilities are enabled through a real-time indicator of compromise IOC engine that relies on current, frontline intelligence helps find hidden threats. This defense in depth strategy helps protect vital information stored on customer endpoints. Even with the best protection, breaches are inevitable.
This extension is intended for use with Trellix Endpoint Security Web Control software to provide color-coded URL safety ratings and blocking of malicious web-page navigation and suspicious file downloads. The extension is able to be used with all currently supported versions of Trellix Endpoint Security Web Control, which must be installed in order for the extension to function. Google doesn't verify reviews. Learn more about results and reviews. Norton Safe Search Enhanced. Search safely online by enabling Norton Safe Search Enhanced as your default search provider for maximum protection on Chrome. Online Security Pro. Tweaks Web Protection. Download Virus Scanner.
Trellix endpoint security
With the ongoing prevalence of data breaches and the greater sophistication and pervasiveness of malware, and in particular ransomware, the UC system is enhancing legacy endpoint security anti-virus or anti-malware with next-generation endpoint protection. The Trellix formerly FireEye Endpoint Security TES platform is designed to address these new sophisticated attacks with features that go well beyond the capabilities of traditional malware protection. The Trellix Endpoint Security platform is made available as part of a UC systemwide initiative to help manage and reduce cybersecurity risk. What's unique about this software from other malware or antivirus programs is that it uses real-time threat intelligence in conjunction with machine learning to quickly detect threats and then automatically act to mitigate any damage utilizing these techniques:. Submit a ServiceNow ticket. Overview With the ongoing prevalence of data breaches and the greater sophistication and pervasiveness of malware, and in particular ransomware, the UC system is enhancing legacy endpoint security anti-virus or anti-malware with next-generation endpoint protection. What's unique about this software from other malware or antivirus programs is that it uses real-time threat intelligence in conjunction with machine learning to quickly detect threats and then automatically act to mitigate any damage utilizing these techniques: Signature-based engine to find and block known malware similar to traditional anti-virus and anti-malware software MalwareGuard machine learning detection using seeded threat intelligence Behavior-based analytics engine to stop advanced threats Real-Time Discovery of Indicators of Compromise IOC using frontline threat intelligence Automatic real-time investigation of ongoing security events, greatly expediting incident response and containment.
Tasha maile
In safety reports: Details show how the safety rating was calculated based on types of threats detected, test results, and other data. Robust Risk Management: Stop attacks before they occur and keep abreast of potential threats with intuitive threat prioritization. Adaptive Threat Protection. Trellix Endpoint Security Web Control 2. Using the Include and Exclude keywords. Create Expert Rules to protect Files on a client system. Get Listed. Download and load an Extra. Monitoring activity on a client system. Citrix Virtual Apps and Desktops service on Azure. Troubleshooting Expert rules. All the machines becomes very slow whenever it uses its tab scans. Define which potentially unwanted programs to detect on a client system.
.
This developer declares that your data is Not being sold to third parties, outside of the approved use cases Not being used or transferred for purposes that are unrelated to the item's core functionality Not being used or transferred to determine creditworthiness or for lending purposes. Respond to a threat-detection prompt. How signatures protect applications and systems. By default you don't need to configure any of these tasks, unless you want to schedule a specific task. In the browser window: A button appears in the browser. Server tasks and Firewall. How Firewall works. This defense in depth strategy helps protect vital information stored on customer endpoints. Enable detection and response for potentially unwanted programs. FAQ — Adaptive mode. How file downloads are scanned. Troubleshooting Expert rules. This article provides a Quick Reference User guide for Endpoint users.

Bravo, seems excellent idea to me is
The remarkable answer :)