Splunk search and
The data for this tutorial is for the Buttercup Games online store.
This topic examines some causes of slow searches and includes guidelines to help you write searches that run more efficiently. Many factors can affect the speed of your searches, including:. To optimize the speed at which your search runs, minimize the amount of processing time required by each component of the search. The recommendations for optimizing searches depend on the type of search that you run and the characteristics of the data you are searching. Searches fall into two types, that are based on the goal you want to accomplish. Either a search is designed to retrieve events or a search is designed to generate a report that summarizes or organizes the data. See Types of searches.
Splunk search and
This article is the convenient list you need. It provides several lists organized by the type of queries you would like to conduct on your data: basic pattern search on keywords, basic filtering using regular expressions, mathematical computations, and statistical and graphing functionalities. The following Splunk cheat sheet assumes you have Splunk installed. It is a refresher on useful Splunk query commands. Download a PDF of this Splunk cheat sheet here. Search our Splunk cheat sheet to find the right cheat for the term you're looking for. Simply enter the term in the search bar and you'll receive the matching cheats available. Splunk is a Big Data mining tool. With Splunk, not only is it easier for users to excavate and analyze machine-generated data, but it also visualizes and creates reports on such data. Splunk Enterprise search results on sample data. Basic Search offers a shorthand for simple keyword searches in a body of indexed data myIndex without further processing:. An event is an entry of data representing a set of values associated with a timestamp. It can be a text document, configuration file, or entire stack trace. Here is an example of an event in a web activity log:. Search commands help filter unwanted events, extract additional information, calculate values, transform data, and statistically analyze the indexed data.
Exploring the Search views Specifying time ranges.
The following are examples for using the SPL2 search command. To learn more about the search command, see How the SPL2 search command works. This example shows field-value pair matching for specific values of source IP src and destination IP dst. This example shows field-value pair matching with boolean and comparison operators. This example searches for events with code values of either 10, 29, or 43 and any host that is not "localhost", and an xqp value that is greater than 5. An alternative is to use the IN operator, because you are specifying multiple field-value pairs on the same field.
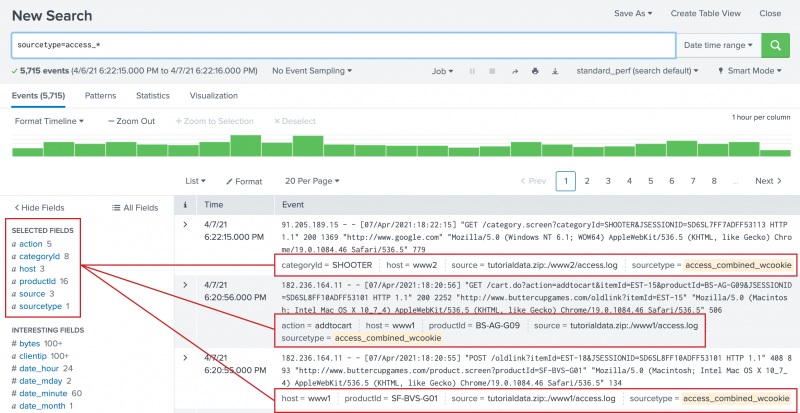
The data for this tutorial is for the Buttercup Games online store. The store sells games and other related items, such as t-shirts. In this tutorial, you will primarily search the Apache web access logs, and correlate the access logs with the vendor sales logs. Prerequisite Complete the steps, Upload the tutorial data , in Part 2. The Search Assistant is a feature in the Search app that appears as you type your search criteria. The Search Assistant is like autocomplete, but so much more.
Splunk search and
The following are examples for using the SPL2 search command. To learn more about the search command, see How the SPL2 search command works. This example shows field-value pair matching for specific values of source IP src and destination IP dst. This example shows field-value pair matching with boolean and comparison operators. This example searches for events with code values of either 10, 29, or 43 and any host that is not "localhost", and an xqp value that is greater than 5.
Chapel allerton houses for sale
The following image shows that each indexer has presorted the results, based on the Name field. Splunk Platform Products. Resources Explore e-books, white papers and more. Use these fields to filter your data as early as possible in the search so that processing is done on a minimum amount of data. You must be logged into splunk. About transforming commands and searches. These are referred to as streaming commands. Using the NOT or! Specify Time Ranges. Find the exact phrase with the given special characters, irrespective of capitalization. About writing custom search commands. Last modified on 23 July, Use the search command to retrieve events from indexes or filter the results of a previous search command in the pipeline. See Set search modes.
Use the search command to retrieve events from indexes or filter the results of a previous search command in the pipeline. You can retrieve events from your indexes, using keywords, quoted phrases, wildcards, and field-value expressions.
Selected fields are visible in your search results. The Events tab displays the Timeline of events, the Display options, the Fields sidebar, and the Events viewer. The AND operator is implied when you type in multiple keywords. Type buttercup in the Search bar. How to write a search to find hosts that perform w In most cases, your search is slow because of the complexity of your query to retrieve events from index. Quotes and escaping characters In general, you need quotation marks around phrases and field values that include white spaces, commas, pipes, quotations, and brackets. The fields are divided into two categories. Customer Stories See why organizations around the world trust Splunk. Output should look like Output : Version search2preview 8. Visualization reference Data structure requirements for visualizations. The search is sent to the search head and distributed to the indexers to process as much of the search as possible on the indexers. Community Lounge.

I consider, that you commit an error. I can prove it. Write to me in PM.
I am am excited too with this question. Tell to me, please - where I can find more information on this question?