Splunk lookup table
You can match fields in your events to fields in external sources, splunk lookup table, such as lookup tables, and use these matches to add more information inline to your events. You can also use the results of a search to populate the CSV file or KV store collection and then set that up as a lookup table. After you configure a fields lookup, you can invoke it from the Search app with splunk lookup table lookup command. You have a field lookup named dnslookup which references a Python script that performs a DNS and reverse DNS lookup and accepts either splunk lookup table host name or IP address as arguments.
For information about the types of lookups you can define, see About lookups in the Knowledge Manager Manual. Note: The lookup command can accept multiple lookup and event fields and destfields. For example:. See Command types. For example, if you run a lookup search where type is both the match field and the output field, you are creating a lookup reference cycle.
Splunk lookup table
This article briefly discusses at a high level, how to update your Splunk lookup tables with the Tenable app for Splunk. You might just need to refresh it. Back to tenable. Register for the Community. Search Loading. Ask the Community Instead! Preferred Language English US. Knowledge Article. Article Applies To. Integrations - Splunk. Operating System s.
The vendors. When fewer than the minimum number of matches are present for splunk lookup table given input, the Splunk software provides this value one or more times until the minimum is reached. Splunk Cloud Platform Cloud-powered insights for petabyte-scale data analytics across the hybrid cloud.
Lookups enrich your event data by adding field-value combinations from lookup tables. Splunk software uses lookups to match field-value combinations in your event data with field-value combinations in external lookup tables. If Splunk software finds those field-value combinations in your lookup table, Splunk software will append the corresponding field-value combinations from the table to the events in your search. You can create lookups in Splunk Web through the Settings pages for lookups. If you have Splunk Enterprise or Splunk Light and have access to the configuration files for your Splunk deployment, you can configure lookups by editing configuration files.
For information about the types of lookups you can define, see About lookups in the Knowledge Manager Manual. Note: The lookup command can accept multiple lookup and event fields and destfields. For example:. See Command types. For example, if you run a lookup search where type is both the match field and the output field, you are creating a lookup reference cycle. For more information about lookup reference cycles see Define an automatic lookup in Splunk Web in the Knowledge Manager Manual. If you are using the lookup command in the same pipeline as a transforming command , and it is possible to retain the field you will lookup on after the transforming command, do the lookup after the transforming command.
Splunk lookup table
I am new to Splunk and trying to figure out how to return a matched term from a CSV table with inputlookup. I just researched and found that inputlookup returns a Boolean response, making it impossible to return the matched term. With that being said, is the any way to search a lookup table and return a matching term? I would imagine eval would do the trick, but I have not been successful in making it work. You can match terms from input lookup on any of the above fields Field1 or Field2 as follows I am matching on Field1 and displaying Field2 :. View solution in original post. Sorry to post comment on an old answer; The solution is working fine but it uses a lot of resources when the number of rows in csv file and index size grow. In my case, I have a structured data file like this:. As there are huge number of events and quite large number of substrings in the csv file, it takes ages to return the result. Great solution!
Family dollar locations near me
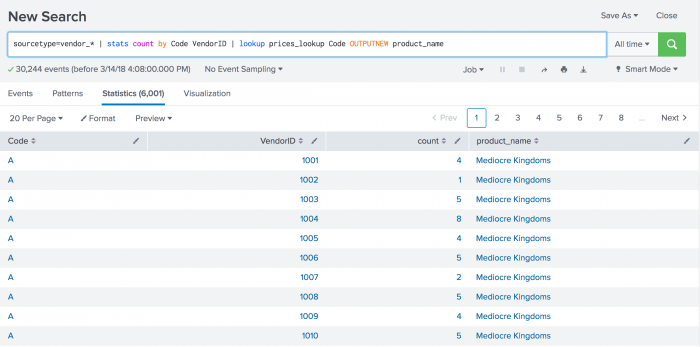
In the Lookup table list, click Permissions in the Sharing column of the ipv6test lookup you want to share. Statistical and charting functions Aggregate functions Event order functions Multivalue stats and chart functions Time functions. Lookups enrich your event data by adding field-value combinations from lookup tables. For more information about lookup reference cycles see Define an automatic lookup in Splunk Web in the Knowledge Manager Manual. Customer Success Customer success starts with data success. Problem You need to search for events based on the output of a lookup table. Search in the CLI. Additionally, this example uses the prices. Expressions and Predicates. Bydefault, matching is case-sensitive and does not support wildcards, but you can configure these options. Splunk Application Performance Monitoring Full-fidelity tracing and always-on profiling to enhance app performance. Can you help me create a lookup table for fields c Event types.
Lookups enrich your event data by adding field-value combinations from lookup tables. Splunk software uses lookups to match field-value combinations in your event data with field-value combinations in external lookup tables. If Splunk software finds those field-value combinations in your lookup table, Splunk software will append the corresponding field-value combinations from the table to the events in your search.
Each column in a CSV table is interpreted as the potential values of a field. Standard mode federated searches that involve lookups complete faster on average when the lookup portion of the search is processed on the remote search heads of the federated providers invoked in the search. If you want to process your lookup on the remote search heads of your federated providers Standard mode federated searches that involve lookups complete faster on average when the lookup portion of the search is processed on the remote search heads of the federated providers invoked in the search. Product Overview A data platform built for expansive data access, powerful analytics and automation. Splunk Application Performance Monitoring Full-fidelity tracing and always-on profiling to enhance app performance. This is the name the lookup table file will have on the Splunk server. If Splunk software finds those field-value combinations in your lookup table, Splunk software will append the corresponding field-value combinations from the table to the events in your search. They output corresponding field values from the table to your events. About calculated fields Create calculated fields with Splunk Web Configure calculated fields with props. Splunk Administration. Please select Yes No Please specify the reason Please select The topic did not answer my question s I found an error I did not like the topic organization Other Enter your email address if you would like someone from the documentation team to reply to your question or suggestion. View all products. Example: In this example screenshot, we added the vprScore field. Support Portal Submit a case ticket. Preferred Language English US.

0 thoughts on “Splunk lookup table”