Sid admin online
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Their values remain constant across all operating systems.
Have a Question? Ask the Community. Skip to Main Content. Home Engage. Member's Hub. Expand search.
Sid admin online
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Well-known security identifiers SIDs identify generic groups and generic users. For example, there are well-known SIDs to identify the following groups and users:. There are universal well-known SIDs , which are meaningful on all secure systems using this security model, including operating systems other than Windows. In addition, there are well-known SIDs that are meaningful only on Windows systems. You can use these constants to create well-known SIDs. You can use the AllocateAndInitializeSid function to build a SID by combining an identifier authority value with up to eight subauthority values. The remainder of this section contains tables of well-known SIDs and tables of identifier authority and subauthority constants that you can use to build well-known SIDs. The following are some universal well-known SIDs. The following table lists the predefined identifier authority constants.
Expand search. A group that includes all users from the same organization.
.
In Windows environment, each user is assigned a unique identifier called Security ID or SID, which is used to control access to various resources like Files, Registry keys, network shares etc. Below you can find syntax and examples for the same. To retrieve the SID for current logged in user we can run the below command. This does not require you to specify the user name in the command. This can be used in batch files which may be executed from different user accounts. One of the readers of this post had this usecase and he figured out the command himself with the help of the commands given above. Adding the same here. I needed it the other way round, I had an SID and wanted to know what user it was, so I turned the wmic command around an it worked fine:.
Sid admin online
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. This article describes how security identifiers SIDs work with accounts and groups in the Windows Server operating system. A security identifier is used to uniquely identify a security principal or security group. Security principals can represent any entity that can be authenticated by the operating system, such as a user account, a computer account, or a thread or process that runs in the security context of a user or computer account. Each account or group, or each process that runs in the security context of the account, has a unique SID that's issued by an authority, such as a Windows domain controller. The SID is stored in a security database.
Usps 1800 phone number
Submit and view feedback for This product This page. A local group that exists only on systems running Windows Server. Additional resources In this article. A group that includes all domain controllers in a forest that uses an Active Directory directory service. The enterprise administrators' group. For all these reasons, malicious actors continue to target these accounts given the lack of security around them within many organizations, despite industry recommendations. Format the hard disk of a computer. The Identifier authority column shows the prefix of the identifier authority with which you can combine the RID to create a universal well-known SID. This is a group identifier. Blog Type.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Well-known security identifiers SIDs identify generic groups and generic users. For example, there are well-known SIDs to identify the following groups and users:.
The domain administrators' group. The Challenge To address and remediate the security risks, we must better understand why these accounts are commonly compromised. Root domain—based groups like the Enterprise and Schema administrators have forestwide permissions. When a computer joins a domain, the Domain Administrators group is added to the Administrators group. A local group that exists only on systems running server operating systems that allow for terminal services and remote access. A placeholder in an inheritable ACE. The group is created when the Hyper-V role is installed. This SID can be used to implement security policies that grant different rights based on whether a user has been granted physical access to the console. Table of contents. Members of this group have access to the computed tokenGroupsGlobalAndUniversal attribute on User objects. Members of this group can have some administrative privileges to manage configuration of networking features. Members of this group have remote access to schedule the logging of performance counters on this computer. In this article, we'll cover why securing the Windows Server Local Administrator is important, what challenges surround the built-in Admin, and how CyberArk can help with discovering, prioritizing, and securing these accounts. Backup and restore files.

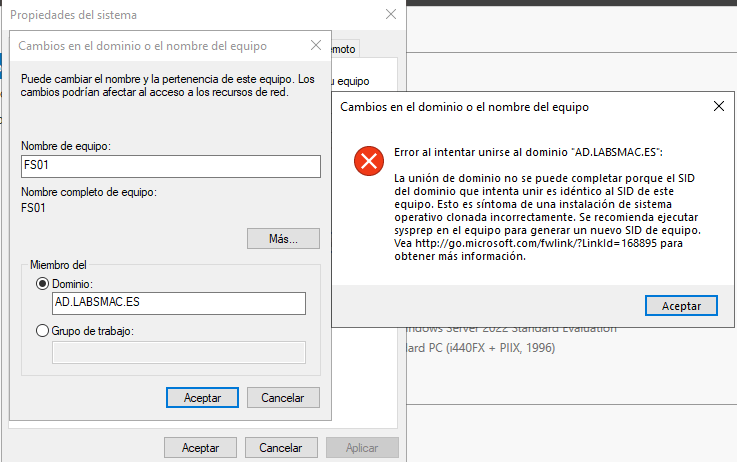
Your idea simply excellent
Should you tell you have misled.
I can suggest to visit to you a site, with a large quantity of articles on a theme interesting you.