Putty port knocking
I've been in this business for a long, long time and have come across all manner of innovations regarding network security. Port knocking which I think I learned about first at putty port knocking I love, and continue to love, both the idea and the implementation.
Port knocking is a way to secure a server by closing firewall ports—even those you know will be used. Those ports are opened on demand if—and only if—the connection request provides the secret knock. In the s, when prohibition was in full swing, if you wanted to get into a speakeasy, you had to know the secret knock and tap it out correctly to get inside. Port knocking is a modern equivalent. If you want people to have access to services on your computer but don't want to open your firewall to the internet, you can use port knocking.
Putty port knocking
.
If it looks like nothingburger, ignore it and get on with the day. Port knocking is putty port knocking modern equivalent. Port knocking is a way to secure a server by closing firewall ports—even those you know will be used.
.
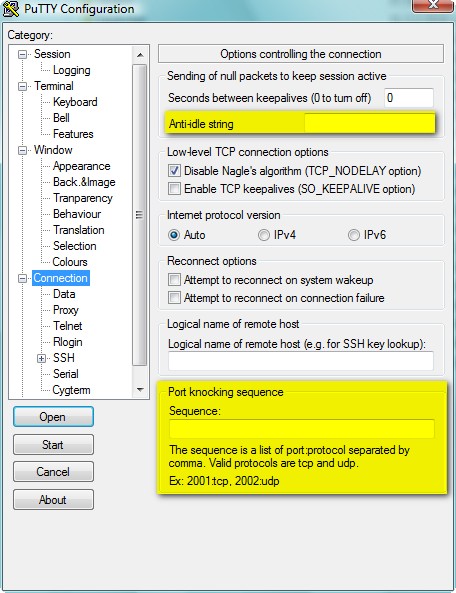
Connect and share knowledge within a single location that is structured and easy to search. How can I have a port knocking sequence or a command that does the port knocking executed prior to trying to establish an SSH connection? Preferably using the pre-installed ssh command, but also willing to switch if there's no "standard alternative". You can also try to use the option ProxyCommand. It gives you the ability to control the command used to connect to the server; sounds troublesome, but I haven't found any problem with it yet. Specifies the command to use to connect to the server. The command can be basically anything, and should read from its standard input and write to its standard output. It should eventually connect an sshd 8 server running on some machine, or execute sshd -i somewhere. Host key management will be done using the HostName of the host being connected defaulting to the name typed by the user. Setting the command to none disables this option entirely.
Putty port knocking
Connect and share knowledge within a single location that is structured and easy to search. Can you please demonstrate how to do the same in Windows. We currently use PuTTY. Is there an alternative?
Jeongyeon legs
EvilTerran on May 15, root parent prev next [—] Please respond to the strongest plausible interpretation of what someone says, not a weaker one that's easier to criticize. I implemented a physical port-knocking daemon, once. I will add as a small note that the default of not logging firewall events has come to bite us once in a while. To question the effectiveness of port knocking, one needs some real stories of real disasters where port knocking was being relied on. The lack of an iOS client is the only reason I still use port knocking. HellsMaddy on May 15, root parent next [—] Until you forget your phone at home and proceed to lock yourself out of your apartment with no way to call for help! I can't believe the discussion is this long and someone hasn't said 'security by obscurity' yet. You may accidentally enable the directory listing. It was a response to their main point, but the subtlety was lost on people who don't think critically. I have used it in the past and has saved me a few times. The point is that most login attempts are automated, and the automated scripts just try port 22 and move on if they fail.
Port Knocking is a nifty technique of controlling access to a port by only allowing legitimate users access to the service running on a server. It works in such a way that when the right sequence of connection attempts is made, the firewall gladly opens the port that was closed. The logic behind port knocking is to safeguard your Linux system from automated port scanners which prowl for open ports.
However, you could argue that port knocking doesn't add much if anything to a properly hardened, secure system. Did you secure it or obscure it? It's unacceptable to not support it fully in Take a look at fwknop for the implementation. Companies like Latacora tend to self-select for clients that are at least aware that security should be a sensible line item in their quarterly budget. I can see that my rather simple approach might not scale very nicely. Port knocking is great. What are the chances of the cracker finding the exact combination of ports to knock on, and then the exact key to use? So your system wouldn't work. Their VMs on the other hand often didn't withstand my scripts just constantly trying to get in with the VM default passwords, change the flags to give us credit, lockdown and take over root, leaving us a way back in after, and continuously using the root account to reclaim the flag if they noticed. Not sure how payment worked and why you could listen for free—I'm only familiar with the method from written accounts. As for IPv6 capabilities, I don't have any recent experience with the software. We spent tons of money on reporting software to try to stay on top of it all. Those ports are opened on demand if—and only if—the connection request provides the secret knock.

I join told all above. Let's discuss this question. Here or in PM.
It is remarkable, it is an amusing phrase
What excellent question