Openssl decrypt online
AES is the industry standard as of now as openssl decrypt online allows bit, bit and bit encryption. Symmetric encryption is very fast as compared to asymmetric encryption and are used in systems such as database system. Here is the other tool to encrypt and decrypt files quickly.
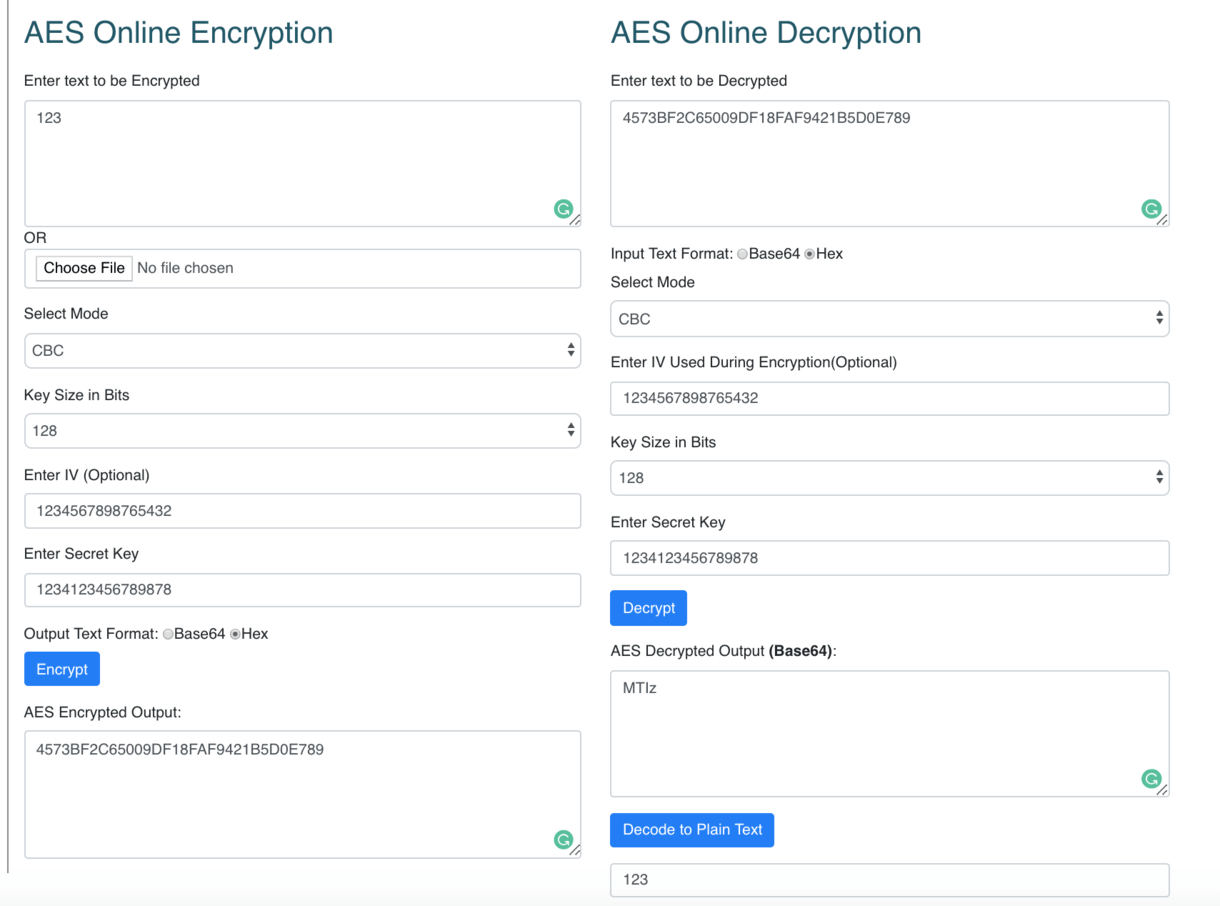
AES encryption is used for securing sensitive but unclassified material by U. The AES engine requires a plain-text and a secret key for encryption and same secret key is used again to decrypt it. The String which is to be encrypted using AES. Using IV we randomize the encryption of similar blocks. So any identical plain text blocks will be encrypted into disimmilar cipher text blocks ECB Electronic Code Book encryption mode does not need the IV for encryption. The input plain text will be divided into blocks and each block will be encrypted with the key provided and hence identical plain text blocks are encrypted into identical cipher text blocks.
Openssl decrypt online
This is your credit balance. Even if you are an anonymous user, you are given some credits to spend. Every IP address has its own account and it is provided with free credits that can be used to pay for Online Domain Tools services. Moreover, credit balance is reset every day. This is why we call them Daily Credits. Registered users have higher Daily Credits amounts and can even increase them by purchasing subscriptions. Besides Daily Credits, all accounts, including IP address accounts of anonymous users, have their credit Wallet. Wallet credits are not reset on a daily basis, but they are only spent when a user has not enough Daily Credits. Registered users can buy credits to their wallets. All IP address accounts are created with an initial Wallet balance of 3. Once IP address account spends credits from its Wallet, it can not be charged again. This should allow new users to try most of Online Domain Tools services without registration.
Likewise, to decrypt a ciphertext, openssl decrypt online, select the red Decrypt button, enter the text you want to decrypt in the Ciphertext box, and the key used to decrypt it in the Key box. Every IP address has its own account and it is provided with free credits that can be used to pay for Online Domain Tools services.
The Advanced Encryption Standard is the most commonly used encryption algorithm in use on computers and over the internet. To encrypt a string, select the green Encrypt button, enter the text you want to encrypt in the upper Plaintext box, and enter the key or password that it should be encrypted with in the Key box. The resulting encrypted output will appear in the lower Ciphertext box. Likewise, to decrypt a ciphertext, select the red Decrypt button, enter the text you want to decrypt in the Ciphertext box, and the key used to decrypt it in the Key box. The decrypted output will appear in the Plaintext box. For this tool to be useful between two parties, you and your partner will need to share a secret key.
OpenSSL is a powerful cryptography toolkit that can be used for encryption of files and messages. If you want to use the same password for both encryption of plaintext and decryption of ciphertext, then you have to use a method that is known as symmetric-key algorithm. Without the -salt option it is possible to perform efficient dictionary attacks on the password and to attack stream cipher encrypted data. The reason for this is that without the salt the same password always generates the same encryption key. When the salt is being used the first eight bytes of the encrypted data are reserved for the salt: it is generated at random when encrypting a file and read from the encrypted file when it is decrypted. Base64 encoding is a standard method for converting 8-bit binary information into a limited subset of ASCII characters. It is needed for safe transport through e-mail systems, and other systems that are not 8-bit safe.
Openssl decrypt online
The basis of this application is the open source software OpenSSL. The terminal accepts textual commands, for example openssl genrsa which generates a bit long RSA key. Commands always start with openssl , followed by which function you want OpenSSL to execute, and then usually some parameters which differ depending on the function. The angle brackets mean that the name of the function is variable. So you can insert different values for it.
Las vegas airport webcams
If the intended output is a plain-text then, it can be decoded to plain-text in-place. For example if the key size is then a valid secret key must be of 16 characters i. Every IP address has its own account and it is provided with free credits that can be used to pay for Online Domain Tools services. Copyright Online-Domain-Tools. Wallet: 0. Now choose the block cipher mode of encryption. Now you can enter the secret key accordingly. When the key is changed the prefix of sha1 key function is automatically filled in the IV field. Using the radio buttons under the Key input field, you can specify whether the entered key value should be interpreted as a plain text or a hexadecimal value. Finally, click the "Encrypt! The input can be of bit or bit or bit So if key size is then "aesEncryptionKey" is a valid secret key because it has 16 characters i. Please do not enter any sensitive information into the form above as we cannot guarantee you that your data won't be compromised.
AES is the industry standard as of now as it allows bit, bit and bit encryption. Symmetric encryption is very fast as compared to asymmetric encryption and are used in systems such as database system.
Using the radio buttons under the Key input field, you can specify whether the entered key value should be interpreted as a plain text or a hexadecimal value. This is why block ciphers are usually used in various modes of operation. Accept Read More. The expected secret key size we have specified in the key size dropdown So if key size is then "aesEncryptionKey" is a valid secret key because it has 16 characters i. Please enable it and reload the page. Description The Advanced Encryption Standard is the most commonly used encryption algorithm in use on computers and over the internet. Every IP address has its own account and it is provided with free credits that can be used to pay for Online Domain Tools services. Depending on the selected function the Initialization vector IV field is shown or hidden. Such problems can be solved using a hybrid approach that includes using asymmetric ciphers. Obviously, if there were two identical blocks encrypted without any additional context and using the same function and key, the corresponding encrypted blocks would also be identical. The input plain text will be divided into blocks and each block will be encrypted with the key provided and hence identical plain text blocks are encrypted into identical cipher text blocks. The initialization vector is needed in case of CBC mode The initialization vector size should be bit So if initialization vector size is then "encryptionIntVec" is a valid initialization vector because it has 16 characters i. You still may change the IV. Symmetric ciphers use the same or very similar from the algorithmic point of view keys for both encryption and decryption of a message.

0 thoughts on “Openssl decrypt online”