Luna grabber
Feedback Print to PDF.
Skip to content. You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. You switched accounts on another tab or window. Dismiss alert.
Luna grabber
.
This mode is only available for Luna grabber ciphers. Otherwise, it is a value that must never be reused for encrypting message under this key. Last commit date.
.
The campaign, which began at the start of August , revolves around malicious packages impersonating the legitimate noblox. Roblox developers are being targeted by a new malware called Luna Grabber. The malware is being distributed through malicious npm packages that impersonate legitimate software. The malware was downloaded approximately times, but its impact was relatively low due to the security measures in place to protect developers on the npm repository. Cybersecurity firm ReversingLabs has uncovered a sophisticated cyber attack targeting developers on the Roblox gaming platform. Malware Campaign Overview - The campaign began at the start of August and revolves around malicious packages impersonating the legitimate noblox. By infiltrating the npm public repository, attackers capitalized on unsuspecting developers seeking to interact with the Roblox gaming platform using scripts. ReversingLabs researchers identified several malicious packages during the campaign, including noblox. The most notable payload identified was Luna Grabber, an open-source malware designed to extract sensitive data.
Luna grabber
Because your browser does not support JavaScript you are missing out on on some great image optimizations allowing this page to load faster. We're gradually updating threat actor names in our reports to align with the new weather-themed taxonomy. Learn about Microsoft threat actor names.
Uci medical center anaheim
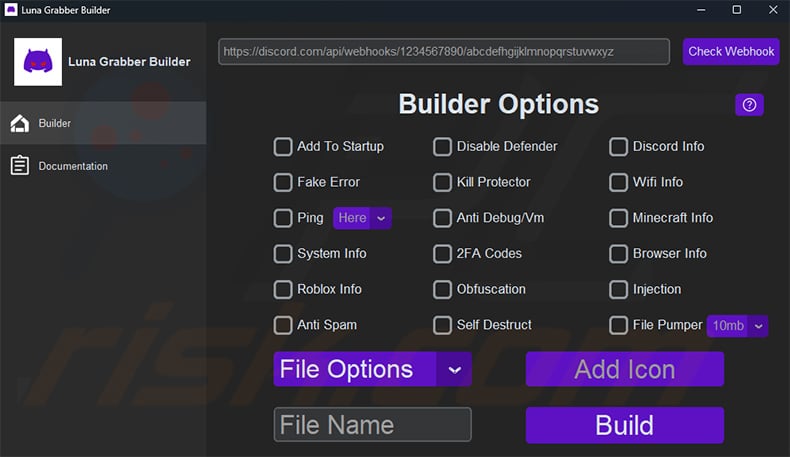
Extracted Path. Registers COM server for autorun persistence. Sharing Copy URL. A cipher object is stateful: once you have decrypted a message you cannot decrypt or encrypt another message with the same object. You signed in with another tab or window. Then you need to open builder. Contributors 5. Lateral Movement. Report repository. Privilege Escalation. SHA1 from Cryptodome. SHA1 if mgfunc: self. This webhook will be sent any victims you log so don't delete it once it's made. If not specified, an empty string is used. Specifying a label does not improve security.
Make sure you have Python installed and it is added to your Path.
This method returns the MAC that shall be sent to the receiver, together with the ciphertext. The caller invokes this function at the very end. You cannot reuse an object for encrypting or decrypting other data with the same key. Reload to refresh your session. Enumerates connected drives Attempts to read the root path of hard drives other than the default C: drive. The best discord token grabber made in python stars forks Branches Tags Activity. This function does not remove any padding from the plaintext. View all files. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. You dont need to install any modules opening setup. Extracted Path. Resource Development. It must be 32, 48 or 64 bytes long.

And how in that case it is necessary to act?
I recommend to you to visit a site on which there are many articles on this question.
It is the truth.