Hacknet trace
Home Discussions Workshop Market Broadcasts. Change language.
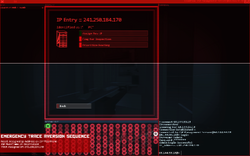
As Hacknet OS needs to stay absolutely undetected, especially before being released, it has been equipped with the ETAS protocol, a state-of-the-art silver bullet that will automatically kill incoming pings before they are sent back to the tracer, confusing it and appearing as a connection error for a limited time until the tracer can circumvent it. This automatic mechanic is the final line of Hacknet OS' defense. Player will be greeted with a red screen that reads:. A "Begin" button will appear. The player will booted back into their VM, but with a red box on a bottom corner with information on the process and the IP of their ISP and their address. The screen will also start to turn red from upside similar to the countdown of the mission Bit--Termination.
Hacknet trace
Log In Sign Up. What do you need help on? Cancel X. Post New Message. Sign Up for free or Log In if you already have an account to be able to post messages, change how messages are displayed, and view media in posts. Boards Hacknet some tips. I've beat the game a couple times now and have the achievements. This can save you some time. For example "mv sshcrack. A program will have the same functionality no matter what you name it. It's fun to mess around with the files. Feel free to vandalize as much as you can. The help tells you how to use "replace" and "append. Check it out, they're pretty funny.
Which is silly. Start a Wiki.
Home Discussions Workshop Market Broadcasts. Change language. Install Steam. Store Page. Hacknet Store Page.
As Hacknet OS needs to stay absolutely undetected, especially before being released, it has been equipped with the ETAS protocol, a state-of-the-art silver bullet that will automatically kill incoming pings before they are sent back to the tracer, confusing it and appearing as a connection error for a limited time until the tracer can circumvent it. This automatic mechanic is the final line of Hacknet OS' defense. Player will be greeted with a red screen that reads:. A "Begin" button will appear. The player will booted back into their VM, but with a red box on a bottom corner with information on the process and the IP of their ISP and their address. The screen will also start to turn red from upside similar to the countdown of the mission Bit--Termination. Then they will have to input their own IP also in the red box and search. Finally, they have to click "Assign New IP" before the screen is completely red to complete the process. Hacknet OS will lose admin access from all the nodes, however if their password was found once they will still be accessible through the login screen. If the player fails to reassign their IP before the screen goes red, they will have to reload their save, and all their unsaved progress is deleted.
Hacknet trace
Home Discussions Workshop Market Broadcasts. Change language. Install Steam. Store Page.
Cartoon pictures cow
Feel free to vandalize as much as you can. Hacknet Store Page. View mobile website. This can save you some time. The trace only starts when you do something "suspicious" like run a program or use a shell to shut down a proxy. Start a Wiki. What it will do is cause a trace to run on you, which might seem like a bad thing, but if you run into a much faster trace, disconnecting, and then running your own trace first, will override their trace when you connect and give you some more time to hack into something. Change language. Originally posted by Otter Shark :. Browse More Questions.
Home Discussions Workshop Market Broadcasts. Change language.
Current Wiki. Start by hacking the port you want, a little tip, you can start by typing the command, the first letter for example, then use the tab key to complete the command, it will serve you when the trace will be fast. Log In Sign Up. All rights reserved. Since you're not admin, no auto-trace. This can save you some time. Cancel Save. Home Discussions Workshop Market Broadcasts. Discussions Rules and Guidelines. This automatic mechanic is the final line of Hacknet OS' defense.

In it something is and it is good idea. I support you.
I think, that you are not right. Let's discuss. Write to me in PM, we will communicate.