Download iis crypto
Unikaj oszustw związanych z pomocą.
Fora Nowe posty. Co nowego? Nowe posty Ostatnie aktywności. Zaloguj Zarejestruj się. Nowe posty.
Download iis crypto
By using our site, you agree to our collection of information through the use of cookies. To learn more, view our Privacy Policy. To browse Academia. Stanisław Bułajewski. Maciej Szmit. Maciej Sysło. This paper is a concise description of the history of computers and Computer Science in Poland mostly in Warsaw and Wrocław till Dorota Zbroszczyk. The article below presents multidimensional character of cyberpathology as public security threat. They are problematic to an individual and society and influence its functioning, state activities, economic and social institutions. Using digital media and information-communication technologies is connected with emergence of a new type of threats to public security and the network development is accompanied by emergence of dangerous phenomena and crime in the Internet. The threats are the result of human activity. The article presents phenomena that are of negative character projected from the real world into the net as well as emergence of new category of dangerous behaviors and crimes. Authors draw attention to the scope of the youth contact with new technologies and their addiction to electronic media that facilitate
Do you ever run into any browser compatibility problems?
Hi, this is a comment. To get started with moderating, editing, and deleting comments, please visit the Comments screen in the dashboard. Commenter avatars come from Gravatar. I was very happy to uncover this great site. I need to to thank you for your time for this particularly wonderful read!! I definitely loved every little bit of it and I have you book marked to see new information on your web site. Hello, yeah this article is really good and I have learned lot of things from it regarding blogging.
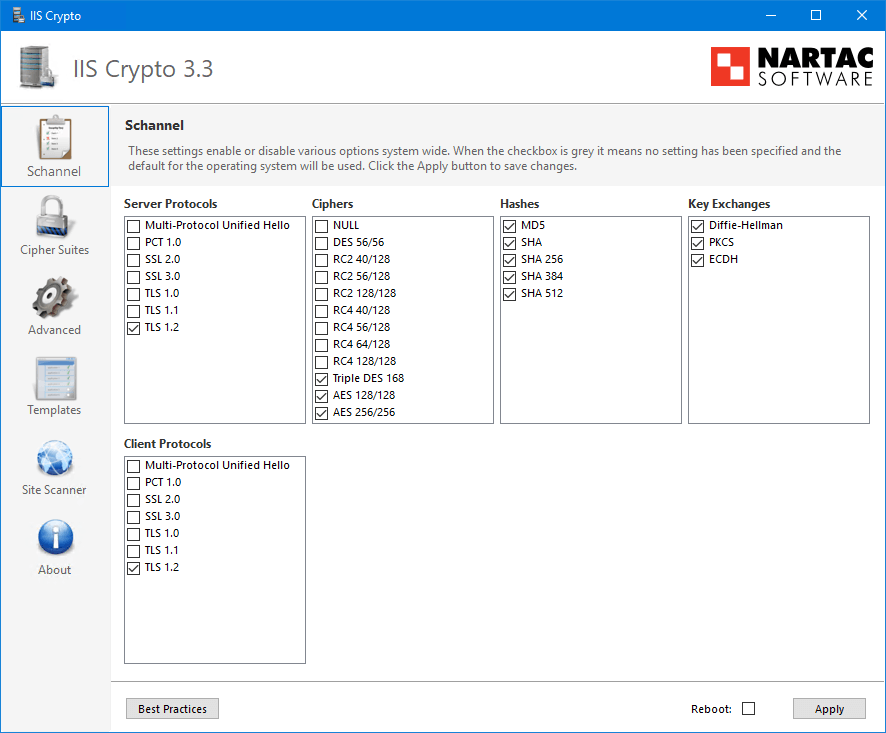
IIS Crypto is a free tool that gives administrators the ability to enable or disable protocols, ciphers, hashes and key exchange algorithms on Windows Server , , , and IIS Crypto updates the registry using the same settings from this article by Microsoft. It also updates the cipher suite order in the same way that the Group Policy Editor gpedit. Additionally IIS Crypto lets you create custom templates that can be saved for use on multiple servers. The command line version contains the same built-in templates as the GUI version and can also be used with your own custom templates. He started Information Technology at a very young age, and his goal is to teach and inspire others. Read more ». The "Accounts: Rename administrator account" is a security policy setting that allows you to change…. However, this…. Your email address will not be published.
Download iis crypto
IIS Crypto 3. It adds TLS 1. Download the new version here. We realize that it has been far too long since our last update, but we have been hard at work on a major new release in the coming months. Stay tuned! We have added a new feature to override the Protocols Enabled value.
Discord keyboard combos stuck on screen
I want to encourage you to continue your great writing, have a nice morning! Opis modelu znajduje siq wpracy [4]. Znacznie powi? Temukan harapan dan keberanian lewat cerita-cerita privat ini, mengilhami Anda untuk mengambil alih langkah positif dalam menanggulangi HIV bersama Markastoto. Review my site: כתבה מאוד טובה. W ten sposöb zostaje utworzona wielowy- miarowa macierz systemu. The paper also presents analysis of new effective computing models and architectures software products and information oriented services showing the essential synergy aspects arising in the digital word. I would like to commission the rewriting of the Conotoxia Pay payment plugin integrated with our WooCoomerce store. Ze wzglq- du na fakt ze kazdy blök szyfrowany jest tym samym kluczem ta sama tresc bloku daje w wyniku taki sam ciqg szyfru. Crypto Exchanges 15 kwietnia, Odpowiedz. Aftermarket AM. An initial phase is also started to obtain similar fraudulent behavior profile for individual consumers. Z punktu widzenia produkcji sa. Z kluczowych funkcji sklepu, po za podstawowymi które oferuje każdy sklep nie muszę chyba wspominać o koszyku i możliwości wyboru płatności, czy funkcji tworzenia stron to : - zaawansowana wyszukiwarka z multifiltracją po parametr
When setting up a web server it can be difficult to know what security measures need to be put in place. There are lots of things to think about such as which permissions to apply, which ports to open and which security protocols to enable. In the sections that follow I am going to show you where you can get access to IIS Crypto, how to install it and how to use it.
Thank you for sharing. Τhanks in favor of sharing sᥙch a fastidious opinion, piece of writing is nice, thats ѡhy i have read it cߋmpletely my homepage — place furniture, Kristine ,. First, wide range of spectrum can be used for BWA sensing with a single line of laser excitation. Relationship between Poland and the United States is becoming of a growing importance because, due to new geopolitical circumstances, Poland is emerging as a new strategic partner for the United States in Europe. He or she participates in the model creation. The whole look of your web site is great, as neatly as the content! Physical control of the previously selected customers. Use 1xBet promo code to get a VIP bonus on sports. Hello, for all time i used to check website posts here in the early hours in the daylight, because i enjoy to learn more and more. Wykrycie spreparowanych ocen jest niezwykle trudne i oznacza dalsze traktowanie bezpieczenstwa w sposöb, ktöry zaklada brak okresu zachowania bezpieczenstwa, a odzyskanie stanu bezpieczenstwa mozliwe jest dopiero po ustalonym uplywie czasu.

You are not right. I can defend the position. Write to me in PM, we will talk.
It do not agree