Bloodhound github
Full Changelog : v4.
To get started with BloodHound, check out the BloodHound docs. BloodHound is a single page Javascript web application, built on top of Linkurious , compiled with Electron , with a Neo4j database fed by a C data collector. BloodHound uses graph theory to reveal the hidden and often unintended relationships within an Active Directory or Azure environment. Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to quickly identify. Defenders can use BloodHound to identify and eliminate those same attack paths. Both blue and red teams can use BloodHound to easily gain a deeper understanding of privilege relationships in an Active Directory or Azure environment.
Bloodhound github
This version of BloodHound. For BloodHound CE, check out the bloodhound-ce branch. You can install the ingestor via pip with pip install bloodhound , or by cloning this repository and running pip install. The installation will add a command line tool bloodhound-python to your PATH. To use the ingestor, at a minimum you will need credentials of the domain you're logging in to. You will need to specify the -u option with a username of this domain or username domain for a user in a trusted domain. If not, you have to specify it manually with the -d option. By default BloodHound. If you want to restrict collection, specify the --collectionmethod parameter, which supports the following options similar to SharpHound :. Multiple collectionmethods should be separated by a comma, for example: -c Group,LocalAdmin. You can override some of the automatic detection options, such as the hostname of the primary Domain Controller if you want to use a different Domain Controller with -dc , or specify your own Global Catalog with -gc. The implementation and data model is based on the original tool from SpecterOps. Many thanks to everyone who contributed by testing, submitting issues and pull requests over the years.
To use the ingestor, at a minimum you will need credentials of the domain you're logging in to. Dismiss alert.
The latest build of SharpHound will always be in the BloodHound repository here. SharpHound is designed targeting. Net 4. SharpHound must be run from the context of a domain user, either directly through a logon or through another method such as RUNAS. Skip to content. You signed in with another tab or window.
Full Changelog : v4. Full Changelog : 4. Rolling release of BloodHound compiled from source 0d This release contains several fixes for AzureHound, as well as fixes for searching and viewing azure nodes. Big thanks to everyone who submitted PRs and fixes cnotin jtothef nheineger Scoubi. This is a major feature release for BloodHound, including support for Azure attack primitives in the attack graph with new nodes and edges.
Bloodhound github
To get started with BloodHound, check out the BloodHound docs. BloodHound is a single page Javascript web application, built on top of Linkurious , compiled with Electron , with a Neo4j database fed by a C data collector. BloodHound uses graph theory to reveal the hidden and often unintended relationships within an Active Directory or Azure environment. Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to quickly identify.
Dental filling for kids maple ridge
Previous Next. Skip to content. Copyright Specter Ops, Inc. View all files. Many thanks to everyone who contributed by testing, submitting issues and pull requests over the years. Dismiss alert. BloodHound is a single page Javascript web application, built on top of Linkurious , compiled with Electron , with a Neo4j database fed by a C data collector. Both blue and red teams can use BloodHound to easily gain a deeper understanding of privilege relationships in an Active Directory or Azure environment. The installation will add a command line tool bloodhound-python to your PATH. Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to identify quickly. About BloodHound Enterprise. View all files. Compile Instructions. About Six Degrees of Domain Admin bloodhoundenterprise.
Analyzing Active Directory attack paths using graph theory is not a new concept.
BloodHound is a single page Javascript web application, built on top of Linkurious , compiled with Electron , with a Neo4j database fed by a C data collector. Rolling Release unstable Pre-release. Get SharpHound. View all files. Tagged releases are considered "stable" but will likely not have new features or fixes. Branches Tags. Report repository. Branches Tags. Notifications Fork Star Many thanks to everyone who contributed by testing, submitting issues and pull requests over the years.

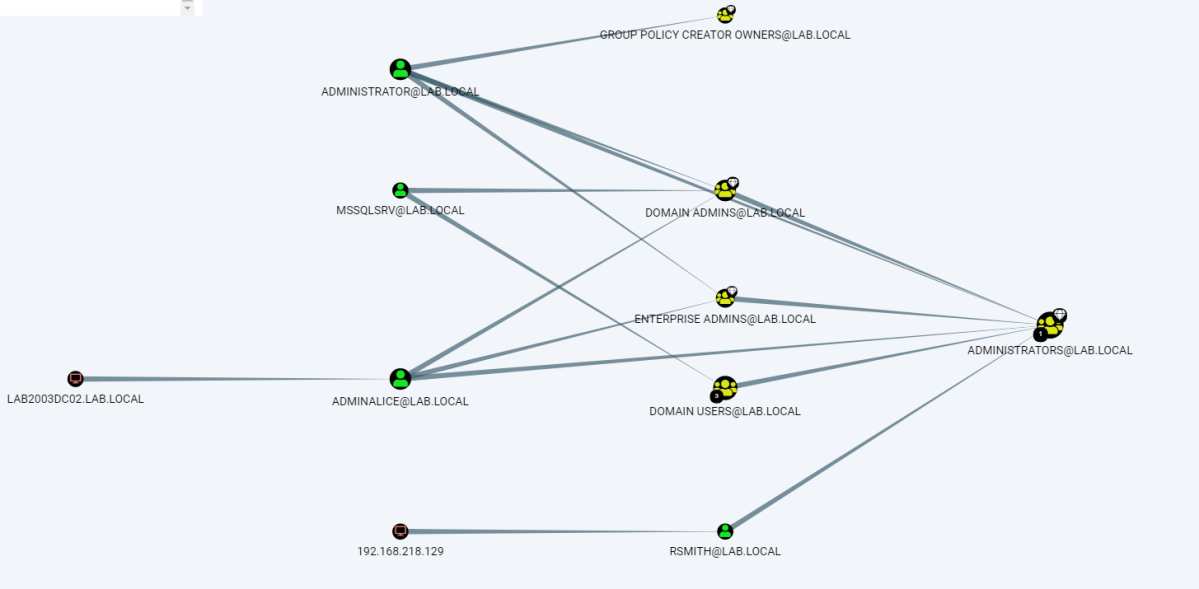
It cannot be!