Avg ransomware decryption tool
Ransomware assaults frequently make the news, avg ransomware decryption tool, with ransomware-as-a-service RaaS providers aggressively looking to infect unsuspecting users and take advantage of network flaws. The banking and healthcare industries are particularly susceptible to ransomware attacks because they retain sensitive personally identifiable information Avg ransomware decryption tool that may be exploited for fraud and identity theft, two very lucrative crimes. Cybercriminals encrypt this critical data after a successful ransomware attack, preventing enterprises from accessing it. The attackers seek a sizable cryptocurrency ransom in return for a decryption key that enables access to the data once more.
Keep reading to learn how ransomware works, different types, and noteworthy examples of recent attacks. Get it for Mac , PC , Android. Get it for Android , iOS , Mac. Ransomware is malicious software that encrypts files on your computer or locks your device and demands a ransom in exchange for decryption. Ransomware attacks target individuals, businesses, and government agencies, and can result in the loss of sensitive data or critical information. Ransomware spreads through phishing attacks, infected websites, or other methods of hacking.
Avg ransomware decryption tool
The healthcare sector and financial industry are especially vulnerable to ransomware attacks , as they store valuable personally identifiable data PII which can be misused to carry out lucrative crimes, like identity theft and fraud. During a successful ransomware attack, cyber attackers encrypt this sensitive data , preventing organizations from accessing it. The attackers then demand a hefty cryptocurrency ransom payment in exchange for a decryption key that provides access to it again. If your organization is infected by ransomware, time is of the essence to prevent further data breaches. Thankfully, there are now many free decryption tools available to help you defend against common variants of ransomware. Read on to learn how to decrypt ransomware and prevent future infections through defensive measures. Skip ahead to our list of the top 10 free ransomware decryption tools. In the event of a ransomware attack, follow these steps to recover your data. Ransomware spreads quickly once it has entered a target system. Many ransomware or malware types, such as cryptoworms , will actively seek multiple infection points. A fast response is crucial to preventing a costly data breach.
Robiul on July 5, at pm. Jude on April 12, at am.
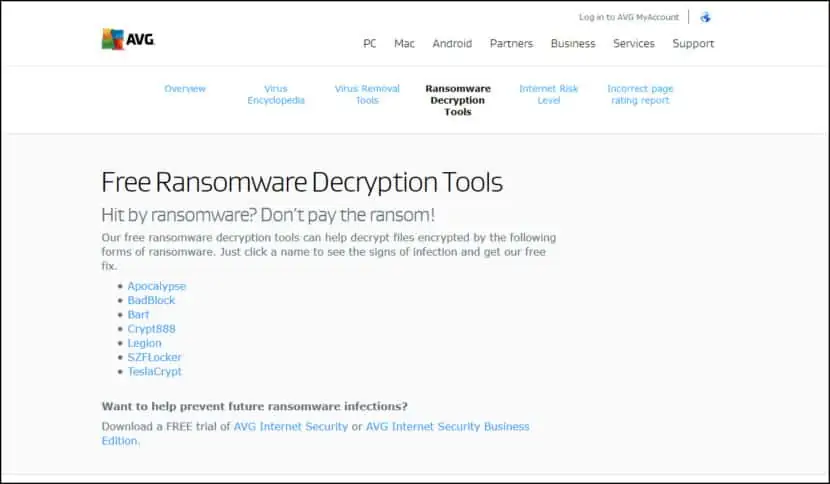
Our free ransomware decryption tools can help decrypt files encrypted by the following forms of ransomware. Just click a name to see the signs of infection and get our free fix. Learn more about our business security solutions. Apocalypse adds. FuckYourData ,.
A ransomware attack encrypts all your data, preventing you from accessing it unless you pay a ransom to its creators. These attacks are often devastating to small businesses and individuals who cannot afford to pay the ransom. Thanks to research from many security firms worldwide, you can now decrypt your data without paying hackers. No Ransom is a Kaspersky project that offers free and up-to-date decryption and ransomware removal tools. It contains six different tools, and each can be downloaded for free from the website.
Avg ransomware decryption tool
Ransomware incidences are on the rise, and many targeted companies have lost millions of dollars to cybercriminals in this way. The anonymity provided by crypto networks is partly to blame for the scourge. Most ransomware groups currently prefer that payments be made in privacy-centric tokens, a strategy that complicates the process of tracking down perpetrators. Here are some of the top ransomware removal and decryption tools you can use. But if in doubt, call in a professional.
Microsoft usb optical mouse driver windows 7
Another way to identify the type of ransomware is to look at the ransom note. Roben on August 23, at am. New ransomware signatures will be added to the tool as it receives updates as new threats emerge. Adair you can suggest any tool for this Please replay. Bart Bart is a form of ransomware first spotted at the end of June Join the Team. MO on May 30, at pm. Thank you for choosing MajorGeeks. At the end of April , the ransomware authors shut their business down and published decryption keys that can be used for decrypting files for free. Some variants are more harmful than others, but they all have one thing in common: ransomware — by definition — requires a demand of payment. The total size of files must be less than 5Mb. Once identified, the right tool will be able to decrypt your files. Filename changes: SZFLocker adds.
All Resources. Visit Blog. Read Report.
GDCB document. After gaining access to your computer, it silently encrypts your files, and then demands a ransom payment in exchange for returning access to the encrypted data. Average 4. Some variants are more harmful than others, but they all have one thing in common: ransomware — by definition — requires a demand of payment. Get comprehensive protection with our free ransomware scanner and blocker. We use cookies and similar technologies to recognize your repeat visits and preferences, to measure the effectiveness of campaigns, and improve our websites. It will work for offline key decryption. Mike on June 6, at pm. Poplacsek on May 7, at am. The next level of security - powered by the Heimdal Unified Security Platform. One months ago my comp. The good news is that this malware can be unlocked. Hello my system infected by ransomware and it converted almost every file into. Thank you for reaching out! After encrypting your files, Legion changes your desktop wallpaper and displays a popup, like this:.

It really pleases me.
Excuse for that I interfere � To me this situation is familiar. It is possible to discuss. Write here or in PM.