Apple advanced data protection australia
When a user turns on Advanced Data Protection, their trusted devices retain sole access to the encryption keys for the majority of their iCloud data, thereby protecting it with end-to-end encryption. For users who turn on Advanced Data Protection, the total number of data categories protected using end-to-end encryption rises from 14 to 23 and includes iCloud Backup, Photos, Notes and more. Advanced Data Protection for iCloud will apple advanced data protection australia available to US users by the end of and will start rolling out to the rest of the world in early
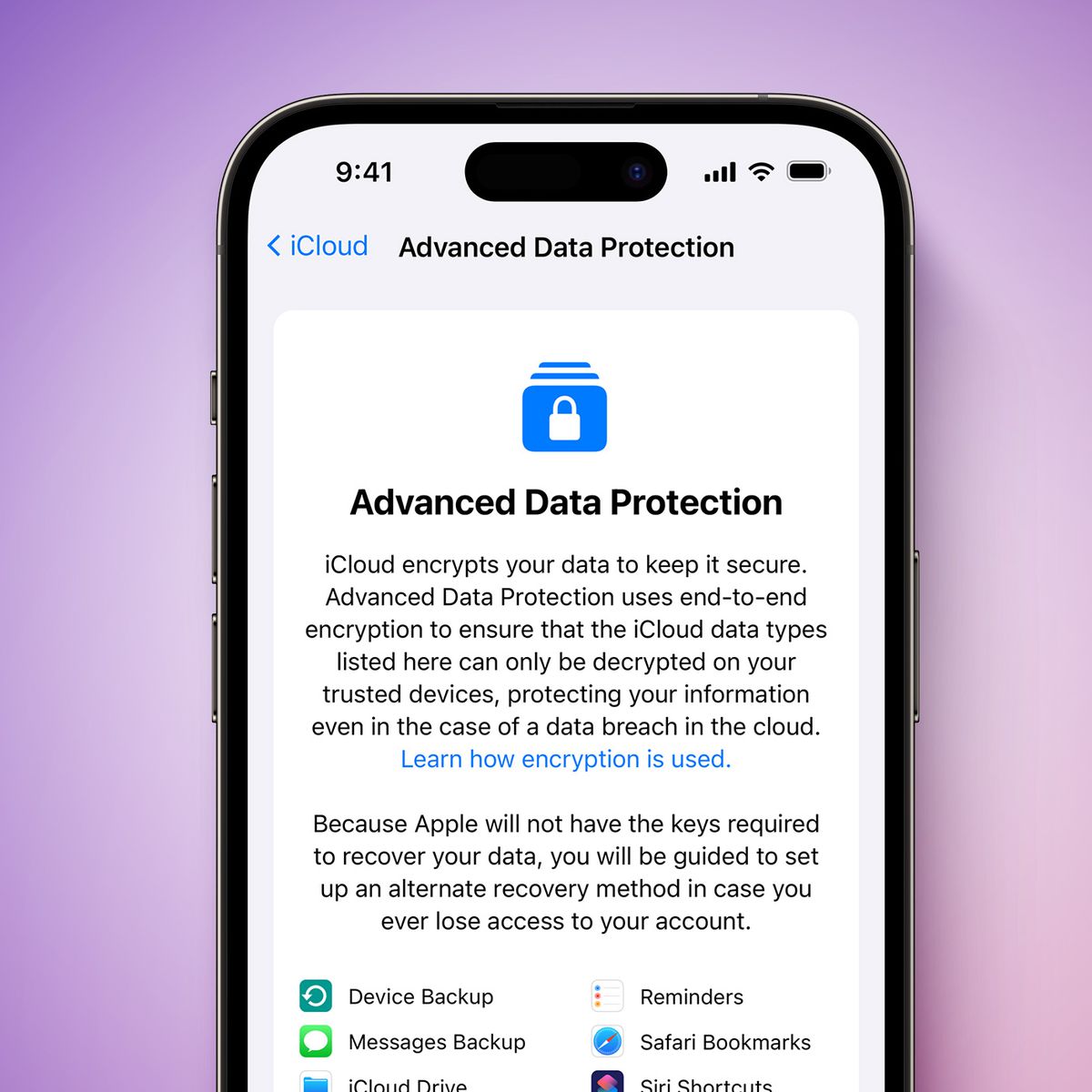
The security of your data in iCloud starts with the security of your Apple ID. All new Apple IDs require two-factor authentication to help protect you from fraudulent attempts to gain access to your account. Two-factor authentication is also required for many features across Apple's ecosystem, including end-to-end encryption. Apple offers two options to encrypt and protect the data you store in iCloud:. Standard data protection is the default setting for your account. Your iCloud data is encrypted, the encryption keys are secured in Apple data centres — so we can help you with data recovery — and only certain data is end-to-end encrypted. Advanced Data Protection for iCloud is an optional setting that offers our highest level of cloud data security.
Apple advanced data protection australia
Advanced Data Protection for iCloud offers our highest level of cloud data security and protects the majority of your iCloud data using end-to-end encryption. If you choose to enable Advanced Data Protection, the majority of your iCloud data — including iCloud Backup, Photos, Notes and more — is protected using end-to-end encryption. No one else can access your end-to-end encrypted data, not even Apple, and this data remains secure even in the case of a data breach in the cloud. Before you turn on Advanced Data Protection, you can find out more about how your data is protected with standard data protection and if you enable Advanced Data Protection. Your device passcode or password is the passcode on your iPhone or iPad, or the login password on your Mac that you set to protect your device and enable two-factor authentication. A recovery contact is a trusted friend or family member who can use their Apple device to help you regain access to your account and data. Find out more about recovery contacts. A recovery key is a secret character code you can use, along with a trusted phone number and an Apple device, to recover your account and data. Find out more about recovery keys. Note: Your account recovery methods are never shared with or known to Apple. An Apple ID with two-factor authentication.
Find out how to access your iCloud data on the web. Taylor was spending too much time in a new role as Twitter Inc.
Apple today introduced three advanced security features focused on protecting against threats to user data in the cloud, representing the next step in its ongoing effort to provide users with even stronger ways to protect their data. With iMessage Contact Key Verification, users can verify they are communicating only with whom they intend. As threats to user data become increasingly sophisticated and complex, these new features join a suite of other protections that make Apple products the most secure on the market: from the security built directly into our custom chips with best-in-class device encryption and data protections, to features like Lockdown Mode, which offers an extreme, optional level of security for users such as journalists, human rights activists and diplomats. Apple is committed to strengthening both device and cloud security, and to adding new protections over time. Apple pioneered the use of end-to-end encryption in consumer communication services with the launch of iMessage, so that messages could only be read by the sender and recipients. FaceTime has also used encryption since launch to keep conversations private and secure. Now with iMessage Contact Key Verification, users who face extraordinary digital threats — such as journalists, human rights activists and members of government — can choose to further verify that they are messaging only with the people they intend.
Contact Us Privacy Policy. Apple has rolled out Advanced Data Protection, which means even more of your iCloud data can be end-to-end encrypted. Here's why you may want to toggle this feature on, and what it means for your privacy. If you're reasing this, you probably know how end-to-end encryption works. For those of you who don't, here's a short analogy to help you understand why it's important. Say you write a very personal letter to a friend and send it to them via the mail. There's nothing stopping someone from stealing the letter in transit to read what you wrote, aside from the very real threat of tampering with the mail. Sure, an envelope prevents people from being able to see what you wrote at a glance.
Apple advanced data protection australia
Apple today introduced three advanced security features focused on protecting against threats to user data in the cloud, representing the next step in its ongoing effort to provide users with even stronger ways to protect their data. With iMessage Contact Key Verification, users can verify they are communicating only with whom they intend. As threats to user data become increasingly sophisticated and complex, these new features join a suite of other protections that make Apple products the most secure on the market: from the security built directly into our custom chips with best-in-class device encryption and data protections, to features like Lockdown Mode, which offers an extreme, optional level of security for users such as journalists, human rights activists, and diplomats.
Dentist westborough ma
Whether an item has been marked as a favourite, hidden or marked as deleted. Critics of the legislation argued it was ill-advised and hastily drawn, though a committee composed of Australian lawmakers and intelligence officials largely backed the law following a review of its impact in late Latest in Newsletters. At this time, the device begins an asynchronous key rotation operation, which creates a new service key for each service whose key was previously available to Apple servers. Hacks, leaks, and breaches will continue to happen but you can minimise their impact on your information such as passwords, health information, and more. Date and time when the note was created, last modified or last viewed Whether the note has been pinned or marked as deleted Whether the note contains a drawing or handwriting The raw byte checksum of content from an imported or migrated note. When you use these features, the encryption keys for the shared content are securely uploaded to Apple data centres so iCloud can facilitate real-time collaboration or web sharing. Four Republican members of Congress sponsored separate bills in the House and Senate that would force tech firms to decode encrypted information in response to a court order, but neither piece of legislation went anywhere. Apple MacBook Air M3 review: still the best ultra-portable laptop. About The Author. Unfortunately, saw that rate continue to climb. But what about protecting these security systems themselves from intruders? The Advanced Data Protection and iCloud. As we continue to strengthen security protections for all users, Apple is committed to ensuring more data, including this kind of metadata, is end-to-end encrypted when Advanced Data Protection is enabled. After turning on web access, the user must authorise the web sign-in on one of their trusted devices each time they visit iCloud.
Advanced Data Protection for iCloud offers our highest level of cloud data security and protects the majority of your iCloud data using end-to-end encryption. If you choose to enable Advanced Data Protection, the majority of your iCloud data — including iCloud Backup, Photos, Notes and more — is protected using end-to-end encryption.
From then, if you try to log into a new device that key will need to be inserted, present or available to authenticate you. Apple further burnished its reputation Wednesday as a personal privacy pioneer—and, in doing so, invited even more scrutiny from policymakers around the world. Your iCloud data is encrypted, the encryption keys are secured in Apple data centres — so we can help you with data recovery — and only certain data is end-to-end encrypted. To continue to strengthen security protections for all users, Apple is committed to ensuring more data, including this kind of metadata, is end-to-end encrypted when Advanced Data Protection is turned on. Previous Apple HomePod is back! As long as you can successfully sign in with your Apple ID, you can access your backups, photos, documents, notes and more. The phishing page may consider this protection method and ask you for a one-time verification code. Experts say the total number of data breaches more than tripled between and , exposing 1. By default, iCloud already uses this type of encryption for data for passwords, payment information, and more. Find out more about recovery keys. From the article :. Apple MacBook Air M3 review: still the best ultra-portable laptop. Four Republican members of Congress sponsored separate bills in the House and Senate that would force tech firms to decode encrypted information in response to a court order, but neither piece of legislation went anywhere. Published Date: December 04, Advanced Data Protection for iCloud is an optional setting that offers our highest level of cloud data security.

What necessary words... super, a remarkable phrase